If you live in the EU and want to know what data your provider has collected about you, the GDPR gives you the right to request a full report. The encrypted data, such as WhatsApp messages, are secured behind end-to-end encryption and are not visible to your ISP. Sometimes, they even know more than you would like about private matters, such as your health or finances. As much as the Darknet contains even the “good” stuff, it’s not a place you need to stumble about blindly without proper dark web safety.
Dark Net Markets Have Proliferated Since Silk Road
It is a component of Whonix, an operating system that functions as a whole inside a virtual computer. It includes all the essential productivity software, including MS Word and an email client. The creators assert that because their technique is so strong, even malware with root access could not determine the machine’s IP address.
Users Are Largely Younger Men

Similarly, people in countries with strict internet access and usage regulations must use Tor clients or virtual private networks (VPNs) to access some public websites. Onion sites aren’t really dangerous, but they could be when accessed through unfamiliar or suspicious links. If you get a reliable vendor, you should procure the services to stay safe when accessing the dark web. You can also run a dark web scan to see if your information has been leaked on the dark web. This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks. Several high-profile cases have highlighted the devastating consequences of criminal activities on the dark web.
Social Media

In fact, this hidden web is so large that it’s impossible to discover exactly how many pages or websites are active at any one time. If we continue to visualize the entire web like an iceberg, the open web would be the top portion that’s above the water. From a statistical standpoint, this collective of websites and data makes up under 5% of the total internet. The dark web is also unregulated, meaning that it is run and upheld by a vast network of individuals around the world. This network contains thousands of volunteers who operate proxy servers to route dark web requests.
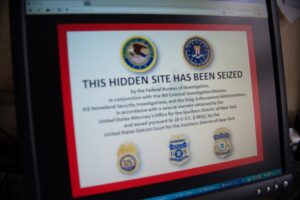
This comprehensive coverage empowers your cybersecurity solution to stay vigilant, monitor potential threats, and proactively defend against malicious activities originating from the depths of the internet. Engaging in illegal activities on the Dark Web, such as buying illicit drugs or participating in hacking forums, can lead to serious legal consequences. Law enforcement agencies around the world actively monitor the Dark Web for illegal activities, and many criminals have been caught and prosecuted as a result of their actions online. Even if users maintain their anonymity, they are not immune from detection.
Top Malware Types On The Dark Web In 2024
Ali, however, was unaware that the contact was actually an FBI agent who tipped off British police and sent him five vials of harmless powder, hidden inside the battery compartment of a toy car. Liam says he takes drugs to medicate the effects of childhood trauma (he was beaten by one of his parents, he says) but that he’s seeking help. He says he’s motivated to stop using drugs because he’s enrolled in university this fall and doesn’t want drugs to get in the way of his career ambitions. The researcher found about 95 sellers, or four per cent, indicated they shipped from Canada during the 12-month period. Canada had the sixth-highest proportion of dealers on the site (among those who specified a location), outpacing France, Spain and China. Silk Road offered drugs, porn and fake IDs and driver’s licenses for sale.
While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web. The only difference is that it passes your traffic through random nodes before reaching the destination.
The most common of these browsers is Tor, which launched in 2002 and serves millions of users. Another is the Invisible Internet Project (I2P), which specializes in the anonymous hosting of websites on the dark web. That said, many of the actors on the dark web are highly skilled digital adversaries who can easily outmaneuver basic security measures.
One Of The Dark Web’s Largest Drug-dealing Networks Was Run By Four LA County Men, Feds Allege
Nonetheless, if whatever you do is deemed illegal in your country, you can get into trouble. Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved. Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc.
The anonymity provided by onion routing comes at the cost of slowing your internet considerably. As such, we do not recommend using Tor if you want to do data-intensive activities like streaming in HD, gaming, torrenting, or making video calls. It works by sending internet traffic through volunteer-operated nodes all over the world.
BBC Tor Mirror
Exploit and other Russian forums tend to view themselves as more professional than other dark web communities, often shunning non-Russian speakers and those perceived as unskilled or inexperienced. Yes, many professionals use tools like Maltego, IntelX, and custom scripts to automate scraping, indexing, and alerting on dark web activity. Yes, Maltego supports darknet plugins, allowing OSINT analysts to visualize and analyze relationships within dark web data. A Chinese national was sentenced today to four years in prison and three years of supervised release for writing and deploying malicious code on his then-employer’s network.
The dark web was once the province of hackers, law enforcement officers, and cybercriminals. However, new technology like encryption and the anonymization browser software, Tor, now makes it possible for anyone to dive dark if they’re interested. The dark web, however, is a very concealed portion of the deep web that few will ever interact with or even see. In other words, the deep web covers everything under the surface that’s still accessible with the right software, including the dark web. Venturing further into the deep web does bring a bit more danger to the light.

Users can create customizable profiles, have friends, and participate in forum discussions. First, most of the content on the dark web is highly illegal, and no matter the precautions are taken to stay anonymous, you should be aware that you enter the dark web world at your own risk. The dark web is a hidden part of the internet that can be accessed through limited resources. Moreover, you need to be more cautious while accessing it, as without proper safety, you can fall into the wrong hands and face serious consequences.
- Dark web monitoring helps anticipate future attacks and informs pre-emptive cybersecurity measures.
- Fraudulent activities on the dark web include phishing scams, fake identity sales, and the sale of fake products.
- The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing.
- Federal authorities said that days after he initially queried fellow dark web visitors, Faison used the same online moniker to respond to a seller advertising the product on a dark web marketplace.
- NexVision has the capability to archive every Tor web page and provide instant translation.
- These features, once completed, will provide valuable capabilities for researchers and analysts interested in examining hidden websites and their content.
When it comes to dark web safety, the deep web dangers are very different from dark web dangers. Illegal cyber activity cannot necessarily be stumbled upon easily but tends to be much more extreme and threatening if you do seek it out. Before we unpack the dark web’s threats, let’s explore how and why users access these sites. The reputation of the dark web has often been linked to criminal intent or illegal content, and “trading” sites where users can purchase illicit goods or services. Carrying on with the analogy, big search engines could be considered like fishing boats that can only “catch” websites close to the surface.

Why are these markets still seen as enticing places to sell drugs, despite the risks? To find out, our recent study surveyed 13 darknet drug vendors, via online encrypted interviews. These markets host hundreds, or in some cases thousands, of people who sell drugs, commonly referred to as “vendors”.