From there, these products are then passed on to distributors, which are the dark web marketplaces in this context. On these marketplaces, they’re listed, sold, and promoted just like items on any e-commerce site. The anonymity and lack of rules that define darknet marketplaces are exactly what make them breeding grounds for fraudulent activities. Of course, the promise of secrecy and unfiltered access might lure you in, but those same features are what make the environment so risky. If you take a quick look through darknet marketplaces, you’ll instantly notice an overwhelming supply of pirated content. We’re talking about even early access to unreleased music, leaked TV episodes, concert footage, and even popular video games before they officially drop.
Explicit And Illegal Content
Abacus Market appeared on the scene in 2021 and quickly became one of the heavyweights among English-speaking markets on the dark web. The categories are well organized, ranging from drugs and fraud to digital products, guides, and malware.What really sets it apart is its focus on security and usability. It supports PGP encryption, two-factor authentication (2FA), alerts against fake sites (antiphishing), and a verification system for sellers. Its interface is easy to navigate, and it has a reliable escrow system, as well as allowing payments with Bitcoin and Monero. All of this has made it one of the most reliable markets still active in 2025.
Silk Road transactions were made with Bitcoin, so it was necessary to exchange cash into Silk Road Bitcoin before purchasing anything — like exchanging cash for tokens at an arcade. All the tokens looked the same, so no one knew where they originated. But a public ledger for transactions (called a blockchain) was kept, so vendors knew the Bitcoin had been transferred. The Silk Road website worked through Tor, which masks user identities by routing encrypted requests through a series of nodes.
The Founder Of Silk Road, Ross Ulbricht
In exploring the top 10 dark-web marketplaces in 2025, we’ve examined their core operations, diverse use-cases, inherent risks, and evolving trends. While these marketplaces continue to serve legitimate purposes, such as enabling secure communication and privacy protection, they also remain hotspots for illicit activities and cybercrime. Technological advancements like AI-driven security, quantum-resistant encryption, and blockchain integration are reshaping the landscape, but simultaneously, global enforcement efforts grow more sophisticated and collaborative.
What Happened To The Seized Bitcoins?
Dark marketplaces Agora, AlphaBay, Dream Market, and Hydra replaced Silk Road and Silk Road 2.0, although all are now defunct. Some current darknet marketplaces include ASAP market, Archetyp, and Incognito, but many former dark web marketplaces have gone mobile on encrypted secure messaging apps like Telegram. Several darknet marketplaces currently exist that follow the Silk Road model, allowing anonymous cryptocurrency transactions on websites only accessible through dark web browsers. Silk Road did at least pay lip service toward limiting the sale of goods that facilitate cybercrime. Today, on Silk Road imitation sites, dark web users can buy and sell private data, cracked passwords, exposed financial details, and more. To help keep yourself protected against these and other online threats, read up on ATM and credit card fraud and the password cracking techniques hackers use.

Criminal Hacking Services
Samwel added that Bryan’s computer, camera and two phones had vanished, which is strange, as Bryan – a small-time Instagram and YouTube celebrity – was inseparable from his devices. He also mentioned that his son had a $400,000 life insurance policy; Njoroge had changed the beneficiary – designating a female friend instead of his parents – just a month before dying. He set up Google alerts for every target’s name – in case something happens to them, even if the authorities have been alerted. That’s how he spotted the news about Bryan Njoroge in a local Indiana outlet, the News and Tribune.
- Even the people – like Chris – who try to enforce the law online are vigilantes, more likely to be arrested than to get the police to bring anyone to justice.
- Of course, the promise of secrecy and unfiltered access might lure you in, but those same features are what make the environment so risky.
- Brian’s Club is one of the best place to buy stolen credit card info, including CVVs, dumps, and even full account packages without revealing your identity.
- Early participants may see some profit, but that money usually comes from new victims, not actual earnings.
- The precedent so far has been acceptably good and I’m less worried about the development of a society without privacy than I otherwise would be.
How To Protect Your Identity While Browsing The Dark Web
Tracking vendor migration—such as from Archetyp to Exodus—provides insight into tactical shifts. Focusing intelligence collection on specialised marketplaces yields better ROI for threat detection and proactive defence. If you’re using a browser like Tor and visiting .onion websites that aren’t accessible through regular search engines or browsers, you’re likely on the dark web. These sites often look basic or outdated, and their URLs are lengthy strings of random letters and numbers.
Listings aren’t public, but it’s steady—think drugs (weed, pills, some synthetics), a few digital extras like cracked accounts. They’ve got 2FA and encryption that’s tighter than a drum, which I’ve tested against crash-prone sites and found solid. Word’s out they’re going decentralized in 2025—less downtime, more trust, right in line with where things are headed.
How Much Is Stolen Data Sold For On Darknet Markets?
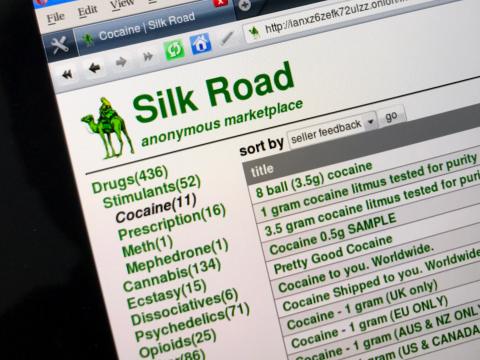
The Silk Road website sold mainly drugs (illegal narcotics, prescription medication), illicit goods (forged documents, pirated media), and some legitimate goods (books, apparel, services). Products such as malware, hacked accounts, or hacking services soon became available. Although guns and other weapons were traded, contract killing services were, allegedly, never officially available on Silk Road. While some of these markets were shuttered by law enforcement agencies – some took the easy way out with exit scams.
Topics And Products Sold
For operations security he suggests avoiding storing conversation logs, varying writing styles, avoiding mobile phone-based tracking and leaking false personal details to further obfuscate one’s identity. Whilst a great many products are sold, drugs dominate the numbers of listings, with the drugs including cannabis, MDMA, modafinil,108109110 LSD, cocaine, and designer drugs. In another infamous case, the administrator of the dark web-based Playpen child pornography site was sentenced to more than 30 years in jail. Steven Chase was caught by the FBI after inadvertently revealing the real internet address of the site. A further 870 people were reportedly arrested in relation to the site. The developers of Tor and organisations like the Electronic Frontier Foundation (EFF) argue that the principal users of Tor are activists and people simply concerned with maintaining their privacy.
Everything You Need To Know About The First Dark Web Market: The Silk Road Website

Ross Ulbricht said much the same thing of the Silk Road, however, and the FBI has shown that it can penetrate the Tor network on more than one occasion. And in the insane event that someone actually attempted to carry out one of these killings, attention would no doubt flood the marketplace. Given the previous lapses in the Silk Road’s security and the resultant arrests and scrutiny, it seems unlikely that anyone would risk outright murder, even on the supposedly anonymous network. Technologies such as Tor and bitcoin have enabled online assassination markets, as described in parts one to nine of Assassination Politics.
They then use it to blackmail users until they pay a ransom. Imagine trusting a site where you’ve been buying or selling for months, and everything seems legit. Some marketplace operators first build trust by running a legitimate platform. While hiring a hacker might sound like something out of a movie, it’s a very real threat. Businesses may use these services to sabotage their competitors, while individuals may seek revenge or simply want access to private information about someone. Plus, there’s a thorough vetting process for new buyers and sellers to keep the community more secure.
As one of PrivacySavvy’s resident VPN experts, he guides readers on protecting their online information and anonymity. Saheed earned his degree in Technology and Ethics from the University of Lagos in Nigeria. Since then, he has dedicated his career to writing extensively about crucial infosec, data privacy, and cybersecurity topics.
Often they give a bit of information about why they want the person killed, which usually gives them away. Or this person should be given a message; that’s for being a cheater. After the order, there’s further negotiations and there’s always a price, how much. Sometimes there’s negotiations about, oh, how can you make sure you don’t take the money and run?

First, the would-be assassin sends his prediction in an encrypted message that can be opened only by a digital code known to the person who sent it. He then makes the kill and sends the organization that code, which would unlock his (correct) prediction. Once verified by the organization, presumably by watching the news, the prize money—in the form of a digital currency donated to the pot—would be publicly posted online as an encrypted file. Again, that file can be unlocked only by a “key” generated by whoever made the prediction. Without anyone knowing the identity of anyone else, the organization would be able to verify the prediction and award the prize to the person who made it.



