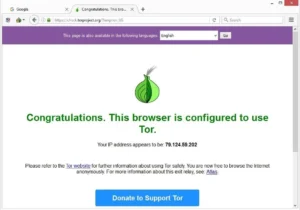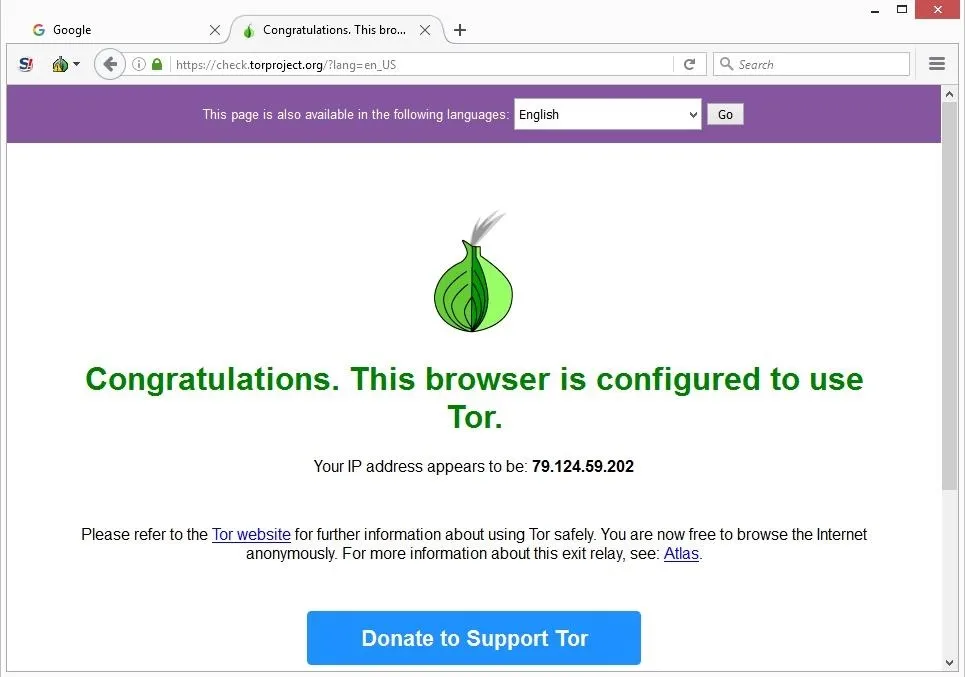
Clicking this button will lead to a series of configuration options designed to help users bypass censorship or accommodate specific network setups. H25.io is a premium directory in the Tor network, offering access to a diverse and meticulously curated list of onion sites. Our mission is to simplify navigation in the complex and evolving world of the darknet.
A VPN app opens another potential vulnerability, as it can log the sites you visit via Tor. If you must use one, ensure it’s a VPN with a strict, independently audited no-logs policy. It encrypts data during transmission to avoid the risk of being eavesdropped. With HTTPS, only you and the website you’ve requested can see the information being exchanged on your browser. For example, in Safer mode, JavaScript is turned off on non-HTTPS (insecure) sites, but in Safest mode, JavaScript is turned off entirely for all sites.
- Tor aims to provide protection for ordinary people who want to follow the law.
- Activities using Tor Browser are subject to the laws of each respective country.
- For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions.
- If you want to surf .onion sites, see our list of the best dark web sites in 2025.
Guide To Accessing Tor Via Tails OS On A USB Thumb Drive:

All this activity, this vision of a bustling marketplace, might make you think that navigating the dark web is easy. The place is as messy and chaotic as you would expect when everyone is anonymous, and a substantial minority are out to scam others. There are also many tools that can be use to monitor the dark web and scan for personally identifiable information and even respond to attacks. Moreover, it’s essential to provide the company staff with enough training as well as defined objectives of what they should look for to bolster the monitoring efforts. Monitoring the deep and dark web is a critical threat intelligence layer that not only authorities worldwide but also users and companies must adapt to.
The United States Naval Research Laboratory developed the technological framework for Tor in the mid-1990s. The Onion Routing project, which became Tor, introduced a publicly available version of the software in 2003. Three years later, a not-for-profit research education organization, The Tor Project, was established to manage the network. The enhanced security and anonymity provided by Tor does come at a cost to the end user. Browsing via Tor is significantly slower than navigating the Web with a standard browser.
Can A VPN And Tor Make The Dark Web Completely Private And Secure?
Tor doesn’t support plugins because they introduce security risks. Malicious actors often target browser plugins to steal website credentials or install malware on unsuspecting devices, so Tor sidesteps these risks altogether. Tor doesn’t support external plugins and extensions, unlike standard browsers. This addon allows you to control which sites can executive JavaScript and which ones can’t. Tor blocks JavaScript by default, but this addon lets you permit it for trusted sites.
The Best Dark Web Links (Tested & Working In
When using this method, Tor will encrypt your request, which will pass through your ISP unhindered. From there, it will go through a VPN server that conceals your IP and wipes geo-locations tags and other elements your Government or ISP might use to track the request. There’s no broad consensus on dark web safety, but you at least need to use Tor and VPN together. Once you have those, there are several ways to tunnel through the dark web. Choosing Tor over standard browsers is crucial for dark web navigation due to its unique privacy features. Tor Browser is supported on any modern Linux-based operating system.
Use Encrypted Communication Apps
The good news is that the platform will not see what you copy/paste. Your data is encrypted in the Tor browser before reaching the ZeroBin servers. ProtonMail is a Swiss-based email service that is very easy to use. You are not required to provide your personal information to create an account. The email service is available both on the surface and on the dark web. The goal of an anonymous and privacy network, Tor, is not to engage in the extensive collection of data.
- Use VPN, avoid logging into personal accounts, enable Tor security settings, and stick to trusted sites.
- Due to certain requirements from Apple, Tor Browser is not available for iPhones, but there are still ways you can connect to the Tor network when using an iOS device.
- While the Tor Browser does an excellent job of protecting your privacy and anonymity, you really shouldn’t use it as your daily driver browser.
- Many of these Reddits have rules prohibiting linking to illegal sites and services, so you likely won’t find anything illegal there.
- The dark web addresses are a randomly-scrambled sequence that generates URLs, mostly hard to remember ones.
- Next, hit the New Circuit for This Site button to connect to a different server chain.
Dark Web Chat/Social Networks
For journalists, students, researchers, and security professionals, it’s a powerful tool when used ethically and safely. Accessing the Dark Web using the Tor Browser is not just about exploring hidden parts of the internet—it’s about understanding privacy and cybersecurity in the modern world. Journalist in India → Uses Tor to access a whistleblowing portal → Submits information anonymously while protecting their identity. To get on the dark web, you need a browser built for the job, and the best in the business is Tor. Tor is a browser engineered for extra security and privacy, and can be used to navigate the normal, surface web as well as the dark web.
Why Do People Use Tor?
Torch is one of the oldest dark web search engines, having served the darknet community for years. It boasts a vast archive of over 400,000 pages, providing comprehensive coverage of .onion sites, including forums, blogs, and marketplaces. Once connected to Tor, you’re ready to begin exploring the dark web. However, keep in mind that the dark web is not organized like the regular internet.
Cracking down on many illegal marketplaces on the dark web is the result of such monitoring. So, you risk being flagged or investigated for visiting certain sites, even without criminal intent. The dark web also offers access to blocked resources in countries with strict government censorship on the internet. Citizens of such countries can use the dark web to bypass firewalls and access global information. Tor Browser is a web browser designed to enable anonymous communication and browsing on the internet. It’s a great choice to protect your online identity and activities from tracking, digital threats, and online surveillance.
This is why I strongly suggest using a Virtual Private Network to protect and enhance all of your online activities. A VPN keeps all of your online activities – including your web browsing, online gaming, streaming, and file-sharing – undercover and safe from being tracked or recorded. Another reason you don’t want to use the Tor Browser for your daily web browsing is that it draws attention to you. The Tor Browser prevents your ISP from seeing what websites you’re visiting, but it does not prevent the ISP from seeing that you’re using Tor.
Regularly Update Your Software
These links containing said random characters and numbers are hard to verify as legitimate or safe. You can start your journey to a safer online experience for $4.99/month for a yearly plan, which allows you to connect 10 devices simultaneously and with a 30-day money guarantee. And since the dark web lacks any real regulation or indexing like the regular web, there is no telling who or what might be waiting in the shadows. All sorts of evil and nefarious individuals with sinister intentions. Because of this, we do not recommend using the dark web without protection. When you download and install the Tor browser on your device, you need to click the “connect” button on the landing page.

Tor Browser already comes with HTTPS Everywhere, NoScript, and other patches to protect your privacy and security. Countries such as China (and its famous “Great Firewall” blocks) may monitor citizens at the Internet Service Provider (ISP) level; if you are using Tor, the usage alone may appear in your records. A VPN can help disguise your use of Tor and your visits to dark web resources. A VPN and Tor should be used together and it is advisable to connect via a VPN to Tor, rather than vice versa, for the best protection possible.
When you open your default browser, Freenet will be ready and running through its web-based interface. Note you should use a separate browser than the one you normally use to help ensure anonymity. Setting up I2P requires more configuration on the user’s part than Tor. I2P must be downloaded and installed, after which configuration is done through the router console. Then individual applications must each be separately configured to work with I2P.

Unraveling The Truth About The NIST’s New Password Guidelines
These include things like NoScript for blocking harmful scripts or HTTPS Everywhere, which forces pages to use the secure protocol over HTTP whenever possible. While Tor may seem complex at first, it’s remarkably user-friendly. By following these guidelines, you can explore the power of privacy while browsing online.