We do not recommend venturing into prohibited, unethical sites on the Dark Web. When you find nasty content, just close all the windows, and Tor will erase your records. If you’re worried about the searches you’ve done on Google, learn how to delete your Google search history.

Are Dark Web Search Engines Useful For Cybersecurity Research, And How?
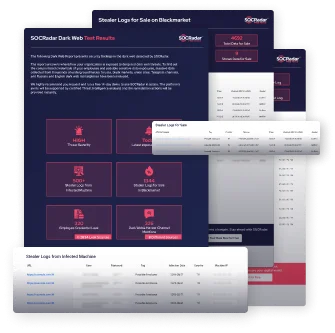
Identity Guard is owned by Aura and is one of the best identity theft protection solutions on the market today. Identity Guard uses your email address to scan the dark web for any compromised data. The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors.
You can add up to five email addresses and run an initial scan that searches deep to find any compromised information linked to the email address. It has a Universal Search engine that automatically allows users to relate Falcon Intelligence Recon results with other CrowdStrike modules. The Express plan is best for SMBs, while the other is for mid-sized and large organizations. Moreover, you can integrate this solution into primary tools like SIEM and SOAR, making it one of the best dark web monitoring solutions. To mitigate these risks while exploring the dark web, it is crucial to use a reputable dark web browser like Octo coupled with proxies for an added layer of security. Keep your software always up-to-date, exercise extreme caution when clicking on links or downloading files, and avoid sharing personal information.
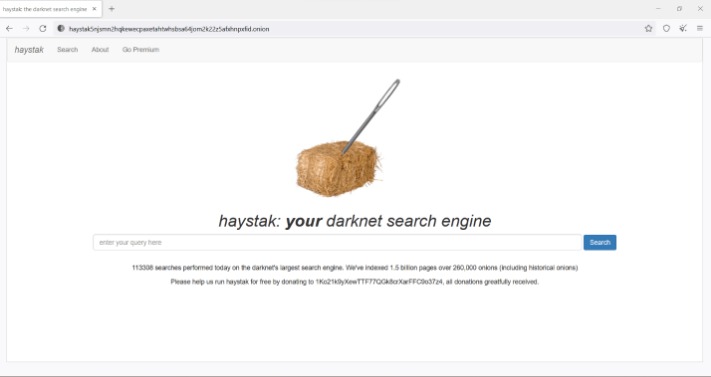
Engines like Ahmia or NotEvil require Tor for encrypted, untraceable searches, whereas deep web crawlers (e.g., for academic databases) use standard browsers and APIs without anonymity emphasis. The dark web subset demands higher security due to potential illicit content, making specialized tools essential. Navigating the dark web is fraught with risks, from malware to legal traps. This expanded section details how to use dark web search engines like Ahmia, NotEvil, or Torch securely, drawing on my 15 years of tech exploration to provide a comprehensive, actionable guide. To provide a rich, authoritative context, here’s an expanded historical evolution of dark web search engines, tracing their development from the early internet to 2025, with NotEvil’s pivotal role. The Hidden Wiki is like a weathered map of the dark web—nostalgic, foundational, but incomplete.
Illuminate Threats, Prevent Attacks With Searchlight Cyber
It is important to use similar tools to shorten the information collection process. Following the dark web from a cybersecurity perspective gives us in-depth information about exciting monetization methods for criminals. By following these techniques and tactics, the next attack can be predicted and creates an essential context for us for pre-attack measures. It’s a lesser-known but highly effective unrestricted search engine ideal for in-depth exploration.
It is the part where we use search engines like Google and includes all the indexed websites and pages. Hunchly is a browser plugin specifically designed for dark web investigations. Its ability to capture browsing activity and maintain audit trails ensures that professionals working in digital forensics and cybersecurity have all the evidence they need to support their findings. Censys provides in-depth visibility into internet-connected assets, including the dark web. It’s a powerful tool for identifying vulnerabilities and potential threats. If you’re concerned about potential threats while browsing, try using our free Cybersecurity Risk Calculator to assess your risk level and take proactive steps to stay protected.

OWASP TorBot
However, using sites like Spokeo should only be done with the best of intentions. You can browse through actual newspaper clips for any topic in a timeline spanning the entire 20th century. When it comes to the right type of research, students, genealogists and more will find this to be the perfect site. If there has ever been a time when you wanted to look at a backlog of the world’s historical newspapers, Elephind is for you.
Can I Get In Trouble For Using The Deep Web?
Some sites might use these details for advertising, analytics, or tracking your online preferences. Make Tech Easier provides tech tutorials, reviews, tips and tricks to help you navigate the complicated world of technology. If it’s to find library books or look through old newspapers, it definitely has its benefits.
Torch prioritizes online anonymity and offers uncensored and unfiltered search results. It also aims to prevent web tracking, enhancing user privacy while searching the dark web. Whether on the clearnet or the dark web, using search engines and other browsing tools can lead to data leaks that expose your search history and other personal information. That’s why it’s important to use online security tools that protect your personal data. While this filtering is intended to improve user safety, it can also prevent access to content that is relevant for research or dark web activity monitoring purposes. This search engine’s indexing is relatively shallow compared to other uncensored engines, meaning many dark web sites remain undiscovered or unlisted.

Provided By International Anti Crime Academy (IACA) The Netherlands
OnionLand’s I2P support signals a shift toward multi-network engines covering Tor, I2P, and Freenet. By 2028, NotEvil’s large index (~32 million sites) could extend to I2P and emerging darknets, creating a unified search platform for dark web ecosystems. Its JavaScript reliance sparked privacy debates, but its ~50,000-site index marked a shift toward user-friendly tools.
What Are Dark Web Monitoring Tools?
- The dark web is a hidden part of the internet that isn’t indexed by search engines and can only be accessed using special tools like the Tor browser.
- They’re essential for secure access but require verification to avoid phishing mimics.
- Its clean, simple interface ensures ease of navigation for a diverse user base including buyers, vendors, and researchers.
- Based in the Czech Republic, its mission is to develop and maintain a massive search engine and data archive.
- Install and launch Tor, adjusting to “Safer” or “Safest” mode in settings to disable JavaScript and enhance security.
To avoid these dangers, always use deep search engines with encrypted connections and advanced filtering options. To use Kilos effectively, begin by accessing it through the Tor browser to ensure privacy. Utilize its filtering options to narrow down search results based on your preferences. For example, if you’re searching hidden services related to e-commerce, filter by shipping origin or currency type to find relevant listings.
- Its large search library, speed, and commitment to user anonymity make it a preferred choice for many people who browse the dark web.
- It also offers a comprehensive list of marketplaces, exchanges, and websites linked to fraudulent activities, helping you stay informed.
- To navigate it safely, it’s crucial to use a reliable VPN, like Forest VPN, alongside the Tor browser to enhance your security.
- We manually collected Tor links and obtained other related links using some tools.
- Sign up for our newsletter and learn how to protect your computer from threats.
Compile/Run From Git Cloned Source
Below is a simple chart for three options that you can use when connecting to a darknet to provide a safer level of protection. Each has varying barriers to entry and users will have different requirements, budgets, or considerations as part of their connection approach. Yes, a dark web scan is worth it because it helps you find out if your credentials have been exposed in a data breach. If your information ends up on the dark web, cybercriminals can use it to access your accounts, steal your identity or launch targeted attacks.
Firefox Monitor Pricing
While it doesn’t index dark web content, it’s the default search engine on the Tor Browser because of its strong privacy features and lack of tracking. For searching within the dark web, specialized tools like Torch are better, as they specifically index .onion sites and hidden content. The World Wide Web Virtual Library is one of the oldest and most reliable online resources. This library provides an array of topics with many information sites that are part of the deep web. For example, this is the place to start if you want to study scientific research, historical documents, or specialized databases.
When used with a dedicated private browser, DuckDuckGo can be a powerful search engine and a potent privacy tool. With the right precautions and tools, you can access the dark web more safely. Use the Tor browser, avoid unfamiliar sites, and be cautious with downloads. However, some significant security risks still remain because the dark web is not regulated. However, Ahmia, Torch, and DeepSearch are among the most commonly used options. Remember, though, that some of them provide no content filtering and may expose you to harmful content.