
Sci-Hub provides free access to scientific papers, with millions of documents. Scientific journals often put their articles behind a paywall and charge high fees for access, but Sci-Hub offers open access to read or download research papers. While it’s a deep resource, it’s also illegal in many countries, because it may violate copyright restrictions, so check out the laws in your area before visiting. Still, since they exist within the dark web, there is a high chance that malicious entities have co-opted one or more for illegal activities. Thus, staying connected to a VPN when you access these sites is vital.

The Hacking Project
Get the latest in privacy news, tips, tricks, and security guides to level-up your digital security. If you only want to mask your IP address and don’t need to access the dark web, then going online with a VPN is much easier and faster than using Tor. While technically not an onion site, we’re including Sci-Hub (sci-hub.se) as an interesting example of a site you can access via Tor. Sci-Hub gives access to millions of scientific papers, mostly ones from behind paywalls. However, due to copyright infringement, Sci-Hub is considered illegal and banned in many countries.
How Does ThreatMon Monitor The Dark Forums?
My tests showed reliable performance for smaller files, but larger transfers can be slow due to Tor’s limitations. Facebook’s official dark web version helps users access the platform in countries where it’s blocked. During testing, I confirmed it provides the same functionality as the regular site while adding Tor’s privacy benefits. The interface works smoothly, but it usually loads slower due to Tor routing. In many places, including the U.S., the UK, and the EU, accessing the dark web is legal for legitimate purposes.
Use The Right Tools: Tor And Beyond
Telegram has become a key tool for cybercriminals thanks to its massive group capabilities, encryption features, and user anonymity. Many of these channels operate almost like Dark Web forums, facilitating the exchange of stolen data, hacking tools, and all kinds of illegal services. Dark web markets have exploded in scale and reach in 2025, becoming the most dangerous hubs for trading drugs, stolen data, and hacking tools. These anonymous marketplaces—operating mainly on the Tor network—are now a primary threat vector for businesses and cybersecurity professionals.
What Are The Best Onion Sites?
- It connects cybercriminals with collaborators for hacking, fraud, and RaaS activities.
- Sinister attracts the attention of its users with topics such as various tools, social engineering techniques, and cracked programs.
- But you must not use it for any illegal or illicit activities or discussions.
- It tracks Tor user activity by region, showing trends in access and adoption without collecting personal data.
- Telegram channels supplement traditional onion sites, blurring lines between the dark web sites and more mainstream communication tools.
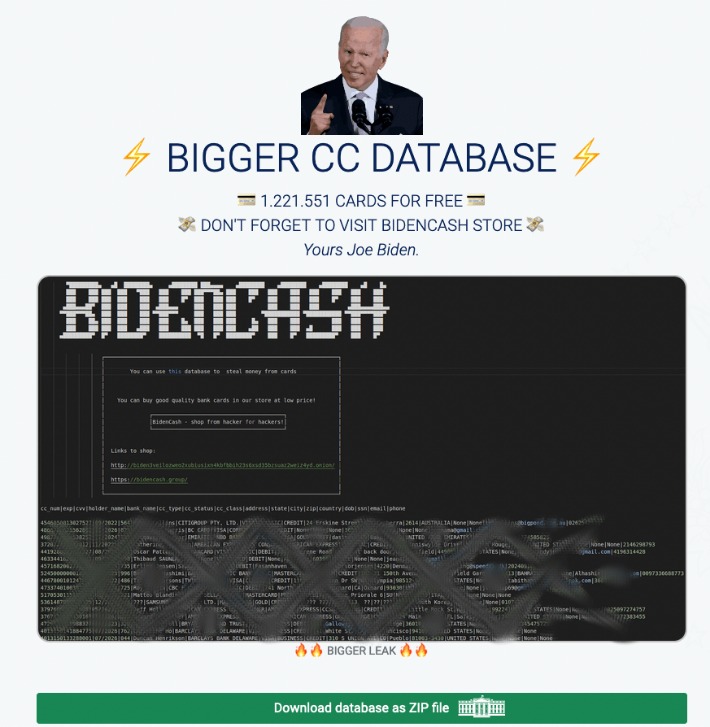
A dark web carding market named ‘BidenCash’ has released a massive dump of 1,221,551 credit cards to promote their marketplace, allowing anyone to download them for free to conduct financial fraud. The Dark Web is just a collection of websites not listed by regular search engines like Google or Bing. Users cannot visit .onion sites using normal browsers like Chrome, Firefox, or Edge. Instead, visitors must access sites on the Tor Network using a special browser developed by the Tor Project.
- These platforms continuously scour the deep and dark web, looking for any traces of your sensitive information.
- SecureDrop uses Tor to provide a safe way for whistleblowers to contact various news outlets.
- The products here include everything from carding tools, carded products, gift cards, fake documents, electronic items, accounts and everything in between.
- Card data on the dark web is a valuable commodity, and it’s often sold on specialized marketplaces known as Card Shops.
- It enhances buyer transparency by importing vendor feedback with PGP proof.
- If you have a good website, you can launch its Tor version, too.
Fraud Documents, Passport, ID Cards, Driving License Services Tor Links
You can send message either publicly, or privately to specific users from the chatroom. Being based out of Iceland, it deletes user data permanently and forever when you delete something. The company has its own VPN, as well as a file encryption software (NordLocker) as well. If they caught you doing direct dealing with a customer to bypass the market, your account will be terminated immediately. Payment is completely wallet-less, no deposits or storage of funds on any market wallet is required.
Cybercriminals Exploit The Death Of Pope Francis

In June 2023, BreachForums made a striking resurgence, three months after its unexpected shutdown, cementing its position as a prominent fixture within the dark web community. This forum takes its name from the popular television series “Breaking Bad” and aims to explore scientific and chemical principles. The primary audience of this platform consists of chemistry enthusiasts, educators, and students, whose objective is to clarify intricate chemical processes and principles.
Their investigative reporting often puts them at odds with influential figures, prompting them to establish a presence on the dark web. This move allows both their journalists and readers to access content securely and evade surveillance. Additionally, the dark web provides a safe channel for whistleblowers to share information with ProPublica without the risk of retaliation. A deep web investigative journalism platform publishing in-depth reports on finance and politics. Leaked credit cards from Telegram channels account for the overwhelming majority of compromised payment card details.
Since most Tor websites are non-indexed and unregulated, the probability of scams is much greater on the dark web. Malicious actors can prey on unsuspecting users without leaving much of a digital footprint on Tor, so it’s often just a matter of time before you run into one. Insights like these help researchers and advocates understand how and why Tor is being used. With this info, the wider online community can grasp Tor’s impact and its ability to provide secure and anonymous internet access. Naturally, this makes the dark web a breeding ground for illegal activity. But onion sites can also serve nobler goals, like providing access to information and independent journalism in countries with government censorship.
Verify All onion Links
The group operates several Telegram channels, the most notable being the DDoSia Project, where they recruit volunteers to carry out coordinated DDoS attacks. In return, participants receive cryptocurrency rewards, incentivizing involvement in these cyber offensives. Your IP is still being revealed to one of the nodes in the onion, meaning your activity and identity can be unmasked. Although profiting from pirated copyrighted material is unethical and illegal, there are some exceptions to using copyrighted material, such as a “private study” provision under UK law.
In some ways, dark web websites offer more browsing freedom, but the lack of safeguards can leave you exposed to hackers, malware, and other online threats, like viruses or other malware. The lack of regulation leaves the dark web rife with offensive content and unsafe websites. Tor Metrics is a set of tools and data provided by the Tor Project that offers insights into the performance, usage, and activity of the Tor ecosystem and its nodes. Besides monitoring and improving the network, the data can be used to detect possible censorship or attacks. Due to the privacy-forward ethos of the Tor project, Tor Metrics stresses that the data it collects must not undermine the anonymity or security of the network. The best dark web websites provide access to educational materials, host secure services, or bypass censorship.

This adaptability makes it challenging for authorities to dismantle these networks completely. Many forums serve as recruitment grounds for cybercriminal groups. Ransomware-as-a-Service (RaaS) groups, for instance, use these platforms to find affiliates and partners. This collaboration expands the reach and impact of their operations. Cybercriminals can purchase or exchange hacking tools, malware, and exploits.



