While the Tor Browser hides your online browsing, it only hides your online activity through the Tor Browser. If you need to protect or enhance your streaming, gaming, or torrenting activities, a Virtual Private Network (VPN) is a much better option as a secure connection to the net. As I mentioned previously, using the Tor Browser will slow down your browsing. Since your traffic goes through a series of relays, getting encrypted or decrypted along the way, things slow way down. This means Tor is a lousy option for streaming video, online gaming, or downloading files (torrenting).
Common Dark Web Threats

The dark web is infamous as a dangerous place, where drugs are bought and hitmen hired, but it can be a safe way to browse the internet if your privacy is serious concern. If you’re going to explore the deepest corners of the internet, make sure you’re doing it with the best armor possible. They hold up under pressure, especially when paired with the Tor browser. Encryption-wise, it uses AES-256, and the free version still includes strong tunneling protocols like WireGuard and IKEv2/IPSec, so you’re not stuck with outdated security. On that note, if you’re having trouble telling the two apart (including their strengths and weaknesses), check out our comparison of Tor and VPNs. Click on the download link for the appropriate version of the Tor Browser.

How To Use Tor Browser Safely
- A handful of dark web search engines that do index .onion sites include NotEvil, Ahmia, Candle, and Torch.
- The criminal groups that developed the malware gets a cut of the affiliates’ earnings, typically between 20% and 30%.
- At the dark end of the web, you’ll find the more hazardous content and activity.
- This signifies that your internet traffic is being routed through the Tor network.
- I2P uses one-way tunnels, so an eavesdropper can only capture outbound or inbound traffic, not both.
Law enforcement agencies worldwide have grappled with the challenges posed by the Dark Web, attempting to balance the need for online privacy with the necessity of combating criminal activities. If you are looking to read combating crime on the dark web online, many resources and platforms are available that shed light on the ongoing efforts to curb the growing threats of cybercrime. On the other hand, the dark web hosts marketplaces and forums where illegal goods and services—such as drugs, weapons, and stolen data—are traded, making it a hotspot for criminal activity. Despite its negative reputation, not all activity on the dark web is malicious; some users rely on it as a tool for freedom of expression or to circumvent restrictions.
Popular Dark Web Search Engines
It will route your traffic through multiple servers instead of one, making tracking your data and activities even harder. A top-of-the-line VPN network that ensures maximum security while accessing dark sites online. The most interesting thing about NordVPN is its built-in Onion over VPN feature. It encrypts your traffic at the entry node and changes your IP address.
Detailed Steps To Access The Dark Web Using Tor
Not every visitor is a criminal, but this is where most cybercrimes begin. Onion links have no regular domain names registered under the domain name registry. Instead, they are designed using a cryptographic key and can be accessed only through software like the Tor browser. One option is to try DuckDuckGo’s .onion version, which is great for privacy. Other options include Ahmia and NotEvil, which focus on listing .onion links.

So, it’s only natural to find ways to keep in touch with your darknet buddies and/or customers. There are several email and IM services which you can use, and it’s highly recommended to pick one if you want to step up your dark web game. The major issue with these websites is that a whopping 50 percent are fake, and there’s no way of telling for sure if they’ll deliver or not. By using Tor, and especially in combination with a VPN, your internet signal is encrypted, making it invisible to your ISP.
Is It Illegal To Visit Dark Websites?
However, effectiveness comes down to how well the tool aligns with your risk profile and operational needs. Analytics Insight is an award-winning tech news publication that delivers in-depth insights into the major technology trends that impact the markets. The content produced on this website is for educational purposes only and does not constitute investment advice or recommendation. Always conduct your own research or check with certified experts before investing, and be prepared for potential losses. Opinions expressed herein are those of the authors and not necessarily those of Analytics Insight, or any of its affiliates, officers or directors.
These sites are only accessible over the Tor network and are commonly used for privacy and anonymity. The Tor Browser also features many built-in protections that protect against tracking and fingerprinting. You can conduct discussions about current events anonymously on Intel Exchange. There are several whistleblower sites, including a dark web version of Wikileaks. Pirate Bay, a BitTorrent site that law enforcement officials have repeatedly shut down, is alive and well there. Most e-commerce providers offer some kind of escrow service that keeps customer funds on hold until the product has been delivered.
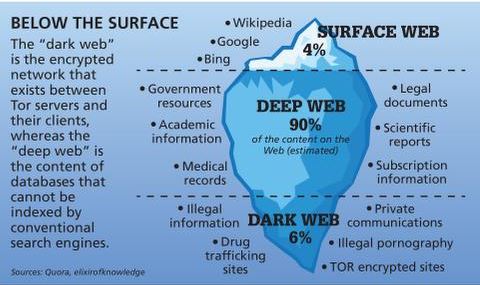
Beyond this “surface web” is the deep web, and within the deep web is the dark web. Then, use data breach monitoring software to help find out if your personal data has leaked onto the dark web. But with the NSA setting up fake exit nodes, and growing concerns about the overall security of the network, you may need a VPN as well, if you want to ensure your privacy.
Afterwards, your request will be matched with the appropriate website. Tricky, but effective; that’s why it’s, by far, the best method to access dark web content. The deep web is just the part of the internet you can’t find with a search engine.
Using Tor Browser: The Final Step To Get On The Dark Web

Second, it allows you to access websites or services that block Tor but accept VPN traffic, such as streaming or banking sites. Finally, it lets you appear as if you’re browsing from a specific country (the country the VPN server you’re connected to is in). Never sign in to any account linked to your real identity (email, social media, banking, etc.) while browsing the dark web. Doing so can tie your activity back to you, destroying your anonymity. If you need to create accounts on dark web services, use a burner email and never reuse usernames or passwords from your real life.
The true internet – that which includes content not indexed by these search engines – is hundreds of times bigger. Content in the dark web is designed to be hidden and you’ll need special software to access it. The Tor browser is the most popular tool, though you can also use Freenet, ZeroNet, I2P, and Riffle. Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software.
This includes evidence of any websites you visit, files you open, passwords you use, and even any other devices or networks you connect to. Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s. The U.S. Army developed “onion routing” to protect intelligence communications online. In 2002 the dark web began to grow significantly when researchers backed by the U.S. Journalists in overly restrictive countries also appreciate the anonymity of the dark web.
The most notorious marketplace to date was Silk Road, an online black market for drugs, which was shut down by the FBI in 2013. Despite this, similar markets have continued to emerge, fueling the Dark Web’s reputation as a haven for illegal trade. There are other ways for spies, hackers or other adversaries to target Tor. Lewis points to the “first contact problem”, when an attacker spots when someone moves from non-private tools to private ones, noting it’s been used to identify whistleblowers. Proton VPN was built by the same folks behind ProtonMail, so privacy is baked into the DNA. The free plan includes unlimited data, strong AES-256 encryption, and a strict no-logs policy governed under Swiss privacy laws (which are actually pretty great for staying off the radar).

Cybersecurity Measures For Protection
Look for features like real-time alerting, coverage of multiple dark web forums and marketplaces, credential and data leak detection, and integration with your existing security stack. Strong vendor support, customizable alerts, and compliance alignment are also key to ensuring the tool delivers actionable insights, rather than just noise. The history of the Dark Web reflects the intricate interplay between technology, privacy concerns, and the ever-evolving landscape of online activities. Malware, ransomware, and hacking tools are also readily available for purchase or rent, enabling attackers to launch sophisticated campaigns. Additionally, forums facilitate the exchange of exploit kits and zero-day vulnerabilities, which can be weaponized before patches are released. The anonymity of the dark web makes it a fertile ground for coordinating cyberattacks and sharing illicit services without detection.


