
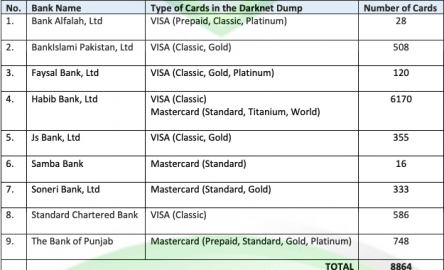
The primary aim of credit card dumps is to illegally obtain and exploit sensitive financial information for fraudulent purposes. They use the stolen credit card information to make purchases or transactions without a cardholder’s consent, often resulting in financial losses for cardholders. Considering this backdrop, it is evident that b1ack’s primary goal has consistently been to profit from the sale or use of these stolen credit card details. By leveraging dark web markets, underground forums, and direct transactions, they aim to capitalize on the extensive reputation and reach they have established through their effective marketing strategy.
Stolen Credit Cards Hit Dark Web For Free
The dark web market for stolen credit card information is a growing concern for consumers and businesses alike. Consumers are advised to protect themselves by monitoring their account statements regularly, using virtual credit cards, and practicing safe online shopping habits. Companies should invest in robust cybersecurity systems and quickly respond to any potential breaches to minimize the damage caused by data dumps. A credit card dump is a significant cybercrime in which an unauthorized digital copy of credit card information is stolen and sold on the black market. Criminals obtain this data through various methods, such as skimming or hacking into payment systems.
Dark Web Prices For Stolen PayPal Accounts Up, Credit Cards Down: Report
- This information helps individuals and businesses understand how hackers target them and whether their data has been compromised in previous breaches.
- These stolen credit cards are often obtained through data breaches or phishing scams.
- In these cases, attackers exploit vulnerabilities in the network infrastructure or software to gain unauthorized access and extract sensitive information from databases.
- If you can, use an online wallet like Apple Pay or Google Pay, says Pascal Busnel, a director with ACA Group, a provider of risk, compliance and cyber solutions.
- If you know about a security breach, contact your credit card issuer right away to put a freeze on your account and cancel & replace your cards.
Social Security numbers and other national ID numbers are for sale on the dark web but aren’t particularly useful to cybercriminals on their own. The average price of a cloned, physical card is $171, or 5.75 cents per dollar of credit limit. Its investigation will focus on whether Optus took reasonable steps to protect the personal details of customers and whether the information collected and retained was necessary to its business. Breachsense monitors the dark web, Telegram channels, hacker forums, and paste sites for external threats to your organization. Network segmentation is absolutely critical for businesses handling card data. Financial institutions tighten their security measures to prevent fraud but that also prevents legitimate transactions as a result.
This is how the site admins encourage users to post their stolen credit card details on their site first. After it relaunched in June 2022, BidenCash initiated a promotional campaign that included sharing a dump of 8 million lines of compromised data for sale, which included thousands of stolen credit cards. In addition to these types of listings, there are other free tools usually available on credit card sites. These tools include for example different types of checkers, which assist threat actors in verifying whether the stolen card information they possess is valid and can be used to make unauthorized purchases. Consumers should monitor their accounts carefully, checking statements regularly for suspicious activity.
Technical Details And Data Sources
- AllWorld.Cards appears to be a relatively new player to the market for selling stolen credit-card data on the Dark Web, according to Cyble.
- Because of data breaches, whether your email address ends up for sale on the Dark Web is often out of your control.
- Leaked credit cards from Telegram channels account for the overwhelming majority of compromised payment card details.
- Unless you live the rest of your life only paying with cash, you’ll never be totally impervious to payment fraud.
In some cases, victims may spend months or even years working to restore their financial situation. Companies that suffer from data breaches are required by law to offer free identity theft protection services to affected customers as part of their response efforts. For companies handling sensitive customer data, investing in robust cybersecurity measures is crucial.
A 2019 data leak of another shop, BriansClub — which appears to have been by a competitor, according to Threatpost —shows how pervasive this trend has become. Angie Ernser is a seasoned writer with a deep interest in financial markets. Her expertise lies in municipal bond investments, where she provides clear and insightful analysis to help readers understand the complexities of municipal bond markets.
After Joker’s Stash Shutdown, The Market For Stolen Financial Data Looks A Lot Different
Not all the above details are available for all 1.2 million records, but most entries seen by BleepingComputer contain over 70% of the data types. The freely circulating file contains a mix of “fresh” cards expiring between 2023 and 2026 from around the world, but most entries appear to be from the United States. Now, the market’s operators decided to promote the site with a much more massive dump in the same fashion that the similar platform ‘All World Cards’ did in August 2021. There’s also a privacy angle—some users live in countries with censorship or surveillance, and the dark web gives them a space to communicate or access information more freely. The second category consists of data stores, which specialize in stolen information.

Underground carding marketplaces are crucial components of the cybercrime ecosystem, they facilitate the sale and purchase of payment card data. One of the most popular carding site was Joker Stash, its operators retired in February 2021 and shut down their servers and destroyed the backups. “The subject release of the credit and debit cards data by BidenCash shop is one of the largest leaks of its kind on any of the cybercrime/underground forums in recent times,” Cyble said.
When making an online purchase, ensure the website is secure by checking for the padlock symbol in the address bar and “https” in the URL. A criminal site known as BidenCash, which uses the president’s name and likeness to trade in stolen data, has just leaked 2,165,700 credit and debit cards online. Dark web credit card fraud poses serious risks to consumers and businesses alike. The goal of this strategy is to create a huge void in the underground marketplace, making room for new shops to emerge and fill the demand for compromised payment cards.
Credit Card Skimming: Understanding A Common Method Of Obtaining Stolen Credit Card Information
What many don’t realize is that much of this stolen data comes from large-scale breaches rather than individual card skimming. Carding has long been a prevalent form of online crime—and it remains a serious threat. One such protection is the use of anti-fraud tools, such as F‑Secure Total, our complete online security solution. These tools offer consumers the most effective way to defend against carding attacks.
Practical Tips To Prevent Carding Fraud

It is important to stay informed about the latest security threats and continuously educate yourself on best practices for protecting your financial information. Joker’s Stash, believed to be the world’s largest online carding store (a forum for selling and buying stolen credit card data), plans to go offline forever on Feb. 15. Researchers from threat intelligence firm Cyble noticed the leak of the payment-card data during a “routine monitoring of cybercrime and Dark Web marketplaces,” researchers said in a post published over the weekend. The cards were published on an underground card-selling market, AllWorld.Cards, and stolen between 2018 and 2019, according to info posted on the forum. Threat actors have leaked 1 million stolen credit cards for free online as a way to promote a fairly new and increasingly popular cybercriminal site dedicated to…selling payment-card credentials.
Check your FICO Score 8 and TransUnion credit report on the go with CreditWise’s secure biometric login. Check your credit score, TransUnion® credit report and more for free— all without hurting your credit score. Using a VPN and Tor browser can help maintain anonymity, but caution should always be exercised to avoid illegal activities.
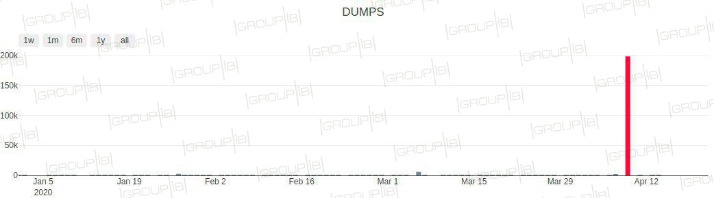
Carding websites continue to find creative ways to promote themselves on legitimate platforms—including global services like Last.fm (music streaming), Gravatar (avatar creation), and Pinterest (visual discovery). This misuse allows cyber criminals to reach a broader audience while evading detection—blending into the digital spaces that consumers and businesses use every day. Fraudsters can use the stolen information for unauthorized transactions, identity theft, or resell the data on other platforms. The scale of this leak underscores the persistent vulnerabilities in global payment systems. By offering free access to such a vast amount of stolen data, the operators aim to build credibility among cybercriminals and entice them to purchase premium services or datasets from their platforms.
It is one of the most active and up to date markets and always provides new and updated malware and data. Our team searched the dark web and put together a list of the most active dark web marketplaces in order to assist you in monitoring illegal trade of products, cybercrime activity, and dark web trends in the dark web space. Strong passwords and security tools add extra layers of defense against cyber threats. These tools scan transactions in real-time, flagging any suspicious charges instantly.
Fraudsters use this data to create counterfeit credit cards or make unauthorized online purchases. B1ack’s Stash, on the other hand, emerged in 2024 and quickly gained attention by releasing millions of stolen credit card details for free—a tactic often used to attract cybercriminals. While it shares a similar purpose with Joker’s Stash, there is no confirmed connection between the two.



