
We recommend you only visit safe dark web links to explore such as The CIA, Facebook, DuckDuckGo, and Torch. Many services that are allegedly offered on the dark web are scams. Some services are genuine; you can get what you want at an agreed fee.
Can Malware Be Present On The Dark Web?
Instead, sites have complex .onion addresses, making them difficult to find without the exact URL. Put simply, the deep web is all the information stored online that isn’t indexed by search engines. You don’t need special tools or a dark net browser to access most of the deep web; you just need to know where to look. Specialized search engines, directories, and wikis can help users locate the data they’re looking for. Because dark web pages generally aren’t indexed, you can’t find them using traditional search engines, but some search engines like DuckDuckGo may help you navigate the dark web more easily.

Marketplaces For Everything Illegal
For example, you can find information unavailable to the public and share data privately while protecting your online identity. Note that most dark web transactions are carried out using Bitcoin or other cryptocurrencies. The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing. It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome. Instead, you need a specific configuration, software, or authorization, such as Tor, to access it.
Step 5: Find Verified Onion Links
Note that Tails’ installation package is the .img format, which means that you’ll need software capable of burning images on your thumb drive. I strongly recommend surfing on the dark web using virtual machine software instead of your locally installed Windows. Because it’s easier to contain malware in a virtual environment, which can be fully controlled. Well, VPN over Tor is basically its opposite – instead of going through the VPN first, the signal passes through the Tor network, before going through the VPN. There’s no broad consensus on dark web safety, but you at least need to use Tor and VPN together. Once you have those, there are several ways to tunnel through the dark web.
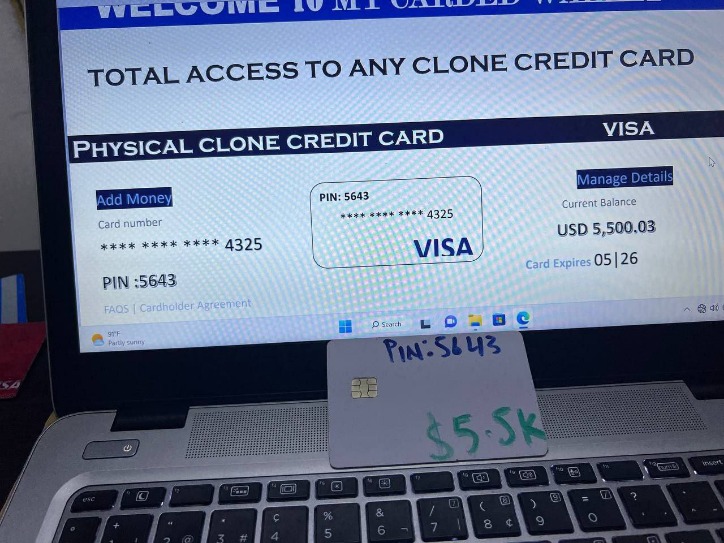
Users leverage these platforms to organize protests, whistleblow, share survival guides, or share files P2P. These are the primary sources of what the general public thinks of as “dark web.” Online marketplaces selling hacked credit cards, fake passports, malware kits, untraceable drugs, anything. Blockchain.info (now Blockchain.com) is a popular cryptocurrency wallet and blockchain explorer service (one of the first sites to launch on the dark web). It was initially created to provide additional security and eliminate cryptocurrency theft. It’s a wallet, explorer service, not a dark web marketplace itself, but still a helpful resource. Cryptocurrencies such as Bitcoin have been the dark web currency even before they became available to the general public.
The best way to find out is to check the “Have I Been Pwned” (HIBP) website. This website allows you to type in your email address or phone number and see if it’s been compromised in any data breaches. If your information has been compromised, then it’s likely that your phone number is also on the dark web. One of the great things about Tor is that it can be used to access both the dark and surface web.
To properly peel back the internet’s layers, you need a tool that provides layers of encryption to hide your activity. Those layers of encryption and routing activity help to anonymize your movements. Keep in mind though, even the Tor browser isn’t an infallible privacy solution.
ExpressVPN is an excellent choice for Tor and accessing the Dark Web. It has a proprietary onion site in the Tor network to give you safe access even if your country restricts VPN usage. The most interesting thing about NordVPN is its built-in Onion over VPN feature.
Step 3: Connect To The Tor Network
It will make your VPN activities seem like normal traffic, so you can use an uncensored internet. However, this feature is only available on iOS, Android, and Windows. In addition, it has an automatic kill switch (Network Lock) that stops traffic if the VPN connection fails.
How Dangerous Is It To Click On Random Onion Links?
If you plan to purchase on a dark net marketplace or dark web commerce sites, you’ll need to create a fake identity. Remember only to make purchases using digital currencies and never provide any online banking login details. The internet is like an iceberg – what we see on the surface is just a small part. Below lies the deep web, a hidden world that standard search engines can’t reach. Inside the deep web, there’s a secretive space known as the dark web.
- By following this dark web access guide, applying Tor browser safety practices, and knowing when it’s safe to browse the dark web, you can navigate responsibly without compromising your security.
- SecureDrop is a site that protects the privacy of journalists and whistleblowers.
- Obviously, finding these .onion websites is the first challenge, as they won’t show up in Google search results.
- However, technological advancements such as encryption and privacy-focused browsers like Tor enabled the general public to access it.
- The dark web, for the uninitiated among you, is a virtual neighborhood beyond the borders of the normal, everyday internet (which includes the website you’re looking at right now).
Most Interesting Sites On The Dark Web??
That means that only 0.024% of all the known pages are findable in Google’s search engine. The users only have access to a fraction of the available data and web pages. The surface web (often referred to as the “visible web”) is the portion of the web available to the general public and indexed in the standard web search engines such as Google, Bing, and Yahoo. Surfshark supports unlimited simultaneous connections to protect as many devices as possible. Also, try its services risk-free with the 30-day money-back guarantee.
While the Tor network is designed to provide anonymity, it alone cannot guarantee your privacy or safety. This section will guide you through the essential preparatory steps and tools to ensure that you remain as protected as possible while exploring hidden services and tor onion domains. The “Dark Web” often conjures up images of hidden marketplaces, illicit trades, and shadowy figures lurking in the digital underworld.
Can Tor Browser Be Used For Regular Internet Browsing?
It’s important to note that although the dark web has many valuable services, it is also a hangout for cybercriminals. The system is designed to provide enhanced security and privacy features. Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity. Be sure that your experience with Whonix will be comparable to Tor because both programs share the same source code. An easy way to find content on the dark web is to receive a link from someone who already knows about it.

The top layer is referred to as the clear or “surface web,” which is what you’re accessing while reading this article. The clear web is made up of websites that you can get to via a search engine like Ecosia or Google. Your clear web browser activity can be logged and tracked by advertisers, governments, and your ISP if you’re not using a VPN. This will help you to remain anonymous and secure at all Tor entry and exit nodes. It uses TrustedServer technology on the entire server network to wipe out your data after every session. This means that there will be no data to track your activities.
But human trafficking, illegal pornography featuring underaged victims, money laundering, and assassinations are also examples of the darkest corners on the dark web. Silk Road became one of the most famous online black markets on the dark web for illegally selling drugs. So, that means that the number of pages increased by over 100 trillion in just over three years. Hypothetically speaking, Google may be aware of well over 200 trillion individual pages (these are obviously NOT all indexed in the search engine).



