
Not every data breach advertisement on the dark web is the result of a genuinely serious incident. By creating hype around what is actually old – and probably irrelevant – data, cybercriminals can provoke publicity, generate buzz, and damage the reputation of both the supplier and its customers. In 2024, we observed a surge in the activity of “drainers” across dark markets. These are malicious tools designed to steal the victim’s crypto assets, such as tokens or NFTs.
Abacus Market Security
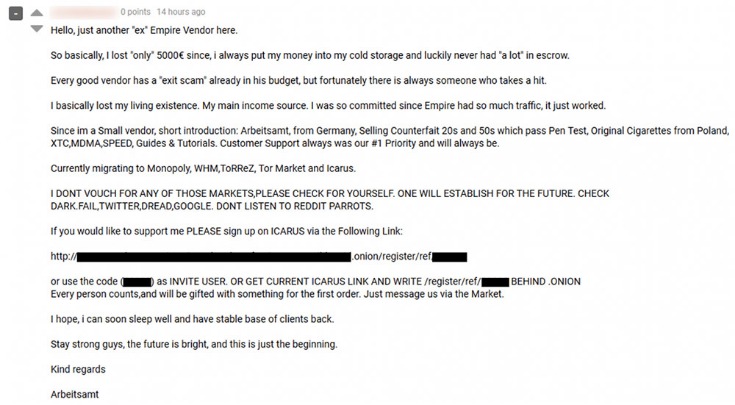
The dark web market hosts a variety of cybercriminal groups, ranging from state-sponsored actors to independent ransomware gangs. These groups operate globally, leveraging sophisticated tools and networks to execute large-scale attacks and maintain anonymity. Darknet markets still play a role in the cybercrime economy, but their future remains uncertain. Law enforcement efforts are increasingly effective, and technological shifts are changing the way these platforms operate. Use this information responsibly and legally—for research, reporting, or educational purposes—not for participation.
Essential Security Measures
It uses the Tor network because it is a popular network that helps to circumvent censorship and online surveillance. Cybercriminals on the dark web marketplace always look for new victims to target them with scams or infect their devices with malware, spyware, or adware. Thus, use the best antivirus software that protects against these online threats. Besides this, it supports wallet-less transactions and accepts payments through Bitcoins, Litecoin, Monero, and Zcash.

Estimates Of Illicit Transaction Activity DO NOT Include:
- Torrez’s 1,500+ vendors—the second largest in our rankings—power its 30,000+ listings, rated 4.7/5 across 45,000+ reviews.
- With over 25,000 active users and a robust escrow system, Alphabay remains a benchmark for reliability and scale.
- Understanding both the lawful and unlawful scenarios helps provide a balanced view of their practical applications in 2025.
- In 2025, 60% of top 10 markets support multiple cryptos—XMR at 40% average, USDT at 15% in ASAP—reflecting a shift from BTC’s 80% dominance in 2023, driven by cost and privacy demands.
- These platforms sell everything from drugs and fake IDs to weapons and hacking tools, resembling a digital black-market bazaar.
The platform’s activity has increased significantly over the past year, indicating its growing influence and market share in the underground economy. Established in 2019, Russian Market is a well-known and highly regarded data store on the dark web, specializing in the sale of PII and various forms of stolen data. Despite its name, the marketplace operates primarily in English and serves a global audience. It has gained a reputation for being a reliable source of high-quality data for cybercriminals.
Monero (XMR): Darknet’s Currency
A timeline of darknet marketplace evolution, from Silk Road to 2025’s top players. IABs are cybercriminals who sell access to compromised networks — often through the dark web — to ransomware groups or other malicious actors. Through threat intelligence platforms, dark web monitoring tools, or by using services that index dark web leaks and credential dumps.
Is The Dark Web Still Active In 2024?
With 25,000+ users and 3,000+ vendors, it’s the gold standard for escrow security and scale. Each of these top-tier markets brings a unique value proposition to the deep web markets ecosystem. Together, they process over $31 million in monthly trades—more than 60% of our top 10’s total—reflecting their outsized impact. Below, we explore their standout features, operational dynamics, and why they’ve earned their elite status. This resource sheds light on how anonymous marketplaces operate, explores Tor-based sites, and shows how digital currencies shape the hidden web economy.
How To Avoid Phishing Scams And Malware Threats
Each offers unique strengths in cryptocurrency trading and escrow security—essential for navigating the onion network. Groups used password-protected channels to trade exploits, stolen data, and malware kits. But as operations scaled, IRC’s static architecture and lack of mobile adoption left it vulnerable. The torch passed to dedicated darknet forums, often on the Tor network, which allowed marketplaces and vendor reputation systems to emerge. Its mobile-first design, ease of channel creation, and semi-anonymous architecture made it an attractive choice for actors who needed speed and reach more than secrecy.
The dark web contains content that’s only accessible through networks like Tor. Tor browsers create encrypted entry points and pathways for the user, so dark web activity remains anonymous. The encryption technology routes users’ data through a large number of intermediate servers, which protects the users’ identity and guarantees anonymity.

Best Dark Web Marketplaces – Detailed List

Whether you want some pharmaceutical products (drugs) or digital items, you will probably find the products here, and that too at affordable prices. Vice City listens to the problems faced by its customers and vendors and solves them so that they can keep using the platform with ease. To access the marketplace, dark web users must register first and pass the CAPTCHA test to prove they are human. Torrez has been steady since 2020, rocking 4,650+ listings with BTC, LTC, ZCash, and Monero.
KEY TAKEAWAYS If you live in a country where you don’t have internet freedom and face extreme … Farwa is an experienced InfoSec writer and cybersecurity journalist skilled in writing articles related to cybersecurity, AI, DevOps, Big Data, Cloud security, VPNs, IAM, and Cloud Computing. Also a contributor on Tripwire.com, Infosecurity Magazine, Security Boulevard, DevOps.com, and CPO Magazine. If the operating system detects any non-anonymous connection, it blocks it, thus ensuring maximum online protection. Always use a fake name and a temporary email address when you buy something from the dark net shops. You can even use a secure email provider or a burner email address whenever you visit the dark web.
- Ulbricht faced several serious charges, including distributing illegal drugs, running a criminal enterprise, hacking, trafficking fake IDs, and money laundering.
- Cybercriminals innovated with multi-language programming (e.g., C++ for client components and Go for server-side panels) and offered tailored solutions to suit specific infection chains.
- Analysts noted that Telegram enabled a shift toward decentralised “broker networks,” where smaller groups coordinated sales of Genesis-style data.
- We developed Lunar to monitor the deep and dark web, including dark web marketplace sites.
- Funds are held until delivery, resolving 90%+ disputes within 48 hours, vs. 40% scam rates in direct deals.
Prioritize Escrow
These anonymous marketplaces—operating mainly on the Tor network—are now a primary threat vector for businesses and cybersecurity professionals. The Silk Road was a famous dark web marketplace where users could buy and sell goods and services anonymously. All the payments were made through cryptocurrency, further enhancing marketplace anonymity.
There’s literally everything on here, and you can find anything from illegal, and legal, drugs, to concert tickets for your favorite band, it’s really quite the digital plaza. Don’t let the humorous name lead you to think this isn’t a serious best darknet market, because it is. This is a rather strange marketplace since it’s quite small and the vendors on the website have been chosen by the owners to sell on the website. Nexus is a reliable marketplace renowned for steady uptime, a roster of vetted vendors, and a battle‑tested escrow engine that shields every deal.



