Cypher invites those seeking an adventurous and continuously evolving journey into the deeper layers of the digital world. Cypher boldly expands its product categories beyond the usual, covering areas like drugs, fraud, hacking, counterfeits, and even defense/intelligence, each with detailed subcategories. Popular items such as cannabis and stimulants are available, but the market shines in its ‘Other’ fraud section, offering unique guides and tools. Cypher also stands out for exclusive offerings like custom hacking services, malware, and sought-after data dumps, reinforcing its status as a trailblazer in the darknet market arena.
SHOW SUPPORTED Privileges
It also works on all platforms, weather its an windows machine, linux, mac, or an android phone. MERGE can be used in conjunction with preceding MATCH and MERGE clauses to create a relationship between two bound nodes m and n, where m is returned by MATCH and n is created or matched by the earlier MERGE. Microsoft Azure customers worldwide now gain access to Active Cypher Cloud Fortress to take advantage of the scalability, reliability. Provides an automated monitoring system for the transcation process. Cypherpunk Holdings, Inc. engages in the investment in technologies and crypto currencies with strong privacy.
The platform acknowledges its growth phase, with its administrators dedicated to implementing significant enhancements for a better user experience. Cypher differentiates itself with an uncluttered yet dynamic approach. Among common items such as drugs and fraud-related materials, the market is a treasure trove of rare and intriguing products, each accompanied by engaging descriptions. It exclusively supports Bitcoin (BTC), Monero (XMR) for transactions, emphasizing the importance of privacy and security, and features a direct payment system for each purchase, catering to the needs of privacy-focused users. The translator supports multiple popular encoding methods including Caesar cipher, Vigenère cipher, and substitution ciphers.
- Powered by advanced algorithms and machine learning, our platform will analyze your browsing and purchasing history to provide you with personalized cypher darknet suggestions tailored to your unique preferences.
- The Cypher pattern forex appears less frequent than other harmonic patterns.
- Grant SHOW TRANSACTION privilege to list transactions on all users on all databases to the specified role.
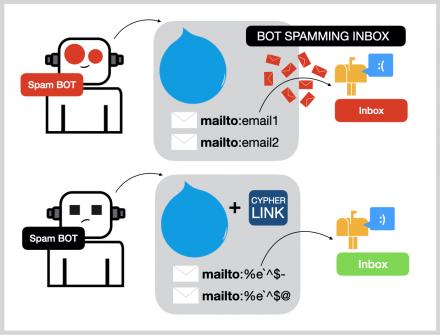
- No useful initialization occurs in this class, creating acipherlink object just prints the dir() function of theclass.
- Grant SET USER STATUS privilege to alter user account status to the specified role.
What Is A Cipher Identifier? (Definition)
The interface is super intuitive, making it perfect for classroom demonstrations. Seamlessly switch between Caesar, Vigenère, and other popular encryption methods. Create varied levels of message security with different coding algorithms. Real-time security for high-frequency trading and financial markets. Takes in the public key and the message, then encrypts the message. No useful initialization occurs in this class, creating acipherlink object just prints the dir() function of theclass.
SHOW FUNCTIONS
The relationships() function returns a LIST containing all the RELATIONSHIP values in a PATH. The nodes() function returns a LIST containing all the NODE values in a PATH. The graph.byElementId() function is used in the USE clause to resolve a constituent graph to which a given element id belongs.If the constituent database is not a standard database in the DBMS, an error will be thrown. The avg() duration function returns the average of a set of DURATION values.
Revolutionizing The Cypher Darknet Shopping Experience
- Revokes the granted and denied privileges to delete composite databases from the specified role.
- The time.realtime() function returns the current ZONED TIME instant using the realtime clock.
- The new approach to execute cypher files is to use the web application called LazyWebCypher .
- The toFloatList() converts a LIST of values and returns a LIST.If any values are not convertible to FLOAT they will be null in the LIST returned.
- Grant ALTER ALIAS privilege to alter aliases to the specified role.
- This cypher url aggregator has completely transformed my shopping experience.
While popular commodities like cannabis and stimulants are readily available, the marketplace excels in its ‘Other’ fraud section, presenting exclusive guides and tools. Cypher’s offerings are further enriched by unique custom hacking services, malware, and coveted data dumps, affirming its pioneering status in the darknet market space. Unlike other online file sharing tools that might expose your files to security vulnerabilities or data breaches, 0xCipherLink ensures end-to-end encryption. Your files are encrypted locally on your machine before being sent over the network, ensuring that only the intended recipient can decrypt and access them.
Explore Properties
The localdatetime.truncate() function truncates the given temporal value to a LOCAL DATETIME instant using the specified unit. The datetime.fromEpochMillis() function creates a ZONED DATETIME given the milliseconds since the start of the epoch. The datetime.fromEpoch() function creates a ZONED DATETIME given the seconds and nanoseconds since the start of the epoch. The toStringOrNull() function converts an INTEGER, FLOAT, BOOLEAN, STRING, POINT, DURATION, DATE, ZONED TIME, LOCAL TIME, LOCAL DATETIME or ZONED DATETIME value to a STRING.For any other input value, null will be returned. The replace() function returns a STRING in which all occurrences of a specified STRING in the given STRING have been replaced by another (specified) replacement STRING. The toIntegerOrNull() function converts a BOOLEAN, INTEGER, FLOAT or a STRING value to an INTEGER value.For any other input value, null will be returned.
ON DATABASE
Property values can be accessed dynamically by using the subscript operator . A subset check using the all() function verifies if all elements of one LIST exist in another. CALL subqueries can execute batches in parallel by appending IN n CONCURRENT TRANSACTIONS, where n is an optional concurrency value used to set the maximum number of transactions that can be executed in parallel. Multiple UNWIND clauses can be chained to unwind nested list elements.
Database Management
Grant DROP ALIAS privilege to delete aliases to the specified role. Grant ALIAS MANAGEMENT privilege to manage aliases to the specified role. Grant SET USER STATUS privilege to alter user account status to the specified role. Grant RENAME USER privilege to rename users to the specified role. Grant USER MANAGEMENT privilege to manage users to the specified role. Grant DROP INDEX privilege to drop indexes on a specified database to the specified role.
As a busy professional, I appreciate the convenience and efficiency of this cypher url marketplace. The user-friendly interface makes it easy to find exactly what I’m looking for, and the fast shipping is a game-changer. I’ve been a loyal customer of this cypher url marketplace for years, and I can honestly say that it’s the best platform I’ve ever used. The selection is unparalleled, and the quality of the cypher mirror products is consistently top-notch.


PocketSuite’s powerful marketing tools help you earn more 4 & 5 Star Reviews from happy customers and use them to win more leads from the most powerful marketplaces in every zip code. This article reveals the top 10 dark web markets dominating in 2025, their unique characteristics, and the critical implications for enterprise cybersecurity. It’s often useful to have a 0th node at the head of a linked list which is always present, but doesn’t represent an actual entry in the list.This 0th node can be locked upon first for any query that needs to alter the list. You can of course break up a larger pattern into smaller ones, and use MERGE on the smaller patterns if needed, when there’s a possibility that a part of this linked pattern already exists. While there is a matching unique Person node with the name Oliver Stone, there is also another unique Person node with the role of Gordon Gekko and MERGE fails to match.

Built using ThirdWeb SDK, ReactJS, Ethers, and TypeScript, Cypher Link aims to revolutionize the way developers connect with supporters and receive funding for their projects through the use of cryptocurrency. On the console I sometimes use curl to talk to Neo4j’s REST interface. That allows me to use the same queries (with references to separate parameters) that I have in my application.You have to wrap the query in your file into a json object for that. Note that each cypher query in the file must end in a semicolon and must be separated by a blank line from the other query. Every PocketSuite account comes with an option to upgrade to a local business phone number for business calls and SMS text.

If true, which is the default, e is the smallest number possible.If false, e is chosen randomly within the list. If randomly choosen,private key generation takes a lot of time, therefore the default is true. Cypher distinguishes itself through its straightforward yet vibrant presentation. Beyond typical offerings like drugs and fraud-related goods, the marketplace is a repository of scarce and fascinating items, each detailed with compelling narratives.
The reduce() function returns the value resulting from the application of an expression on each successive element in a list in conjunction with the result of the computation thus far. The range() function returns a LIST comprising all INTEGER values within a range bounded by a start value and an end value, where the difference step between any two consecutive values is constant; i.e. an arithmetic progression. The keys() function returns a LIST containing the STRING representations for all the property names of a NODE, RELATIONSHIP, or MAP. The duration.inSeconds() function returns the DURATION value equal to the difference in seconds and nanoseconds between the two given instants. The duration.inMonths() function returns the DURATION value equal to the difference in whole months between the two given instants.



