This makes it extremely difficult to find out who you are transacting with. Wasabi is one of the most popular cryptocurrency wallets on the dark web. ZeroBin is a wonderful way to share the content you get from dark web resources. It is a reliable messaging tool where you copy/paste a text or image and send it to your addressee.
Goods And Services Traded On The Dark Web
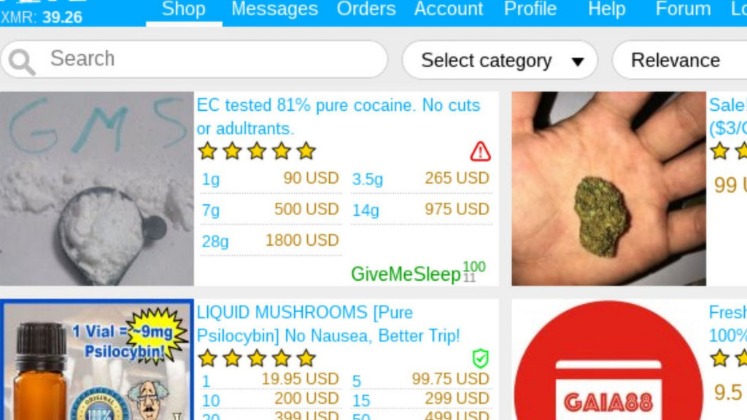
The goal is simple — make financial fraud easy and get as much attention as possible. From drug sales and breached data to scam services and malware, dark web markets are some of the most dangerous corners of the internet. These markets mimic traditional e-commerce websites, but instead of second-hand books or vintage jackets, they traffic in illegal goods and criminal services.
If a seller encourages you to opt for other well-known and commonly used payment methods, then the person is likely to be a scammer, and you must not make any deal with them. When you use it, all the web traffic automatically routes through Tor. If the operating system detects any non-anonymous connection, it blocks it, thus ensuring maximum online protection. In 2013, the FBI shut down the Silk Road, but it was later relaunched in 2014 with the new name of Silk Road 2.0, but the German authorities shut it down in the same year. Other than the Silk Road 2.0, similar marketplaces also emerged, but they all went down sooner or later. The website has a sleek design and interactive user interface, making it the most preferred choice in terms of user experience.
How To Protect Your Data From The Dark Web
Some now offer customer support, escrow systems to prevent fraud, and even user-friendly interfaces that make illegal trade feel strangely routine. Still, the dangers are severe — exposure to scams, malware, surveillance, and prosecution are just the beginning. The very first of these marketplaces to pair the darknet with Bitcoin was the Silk Road. Over the next two years, the Silk Road set the standard for darknet marketplaces. By the time it was shut down in October 2013 and Ross Ulbricht arrested, the site had traded an estimated $183 million worth of goods and services.
Words Of Caution When Using Dark Web Sites
They employ various techniques, such as tracking and infiltrating dark markets, developing advanced threat intelligence, and enhancing international cooperation. As darknets and dark markets continue to evolve, understanding their dynamics and implications is crucial for fortifying the cybersecurity defenses of individuals, organizations, and nations in the digital age. The dark web is a part of the internet that isn’t indexed by search engines.
Data Availability
It’s important to only visit trusted sites and avoid clicking on suspicious links. Discover how to explore black market links safely with essential tips and tools to ensure your online privacy and security. HSI New York leads and directs all operational and administrative activities of the El Dorado Task Force (EDTF). The EDTF encompasses a standalone Cyber Division as part of an effort to stay abreast of emerging criminal threats and in keeping with current and future investigative priorities. The EDTF’s mission is to disrupt, dismantle or render ineffective organizations involved in the laundering of proceeds of narcotics trafficking and other financial crimes. Since its inception in 1992, the task force has been responsible for the seizure of approximately $600 million and more than 2100 arrests.

How Do I Access The Dark Web?
All in all, it is not illegal to access the dark web, but it can create issues for you. If you don’t take the necessary measures, many unsavory activities can expose you to unnecessary risks. With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential.
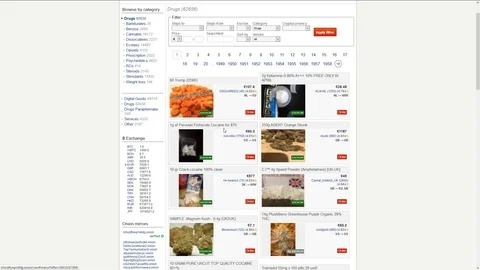
- Until the end of 2013, when Silk Road is the dominant market (see Fig. 3), market-only sellers is the dominant category, and there are no multisellers.
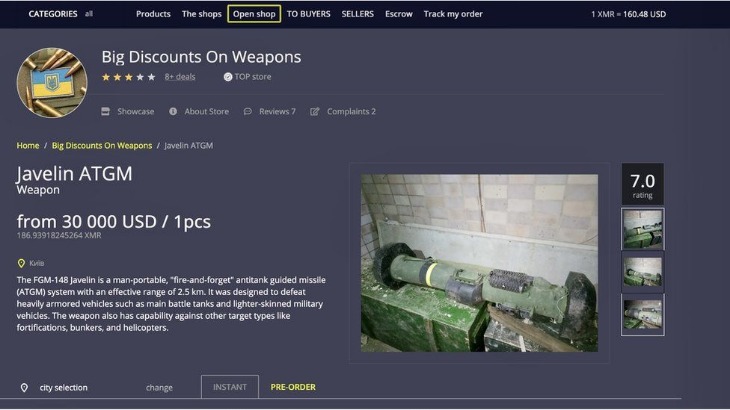
- Purchasing or selling illegal goods—such as controlled substances, counterfeit documents, or stolen data—can result in significant legal penalties, including fines, criminal charges, and imprisonment.
- Some markets are invite-only or have strict registration rules to keep out scammers and law enforcement.
- Either way, no one is accessing the Dark Web with a sense of optimism.
Bear in mind too that laws about freedom of speech and censorship vary from country to country, which is part of the reason the dark web exists in the first place. Individual sites on the dark web look much like they do on the regular web, though a lot of them are a bit more rough around the edges. (Presentation and polish isn’t quite so important on this part of the internet.) Click on any website link, and it’ll appear on screen, with its address at the top. Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS. While there are other browsers you can use to get on the dark web, Tor is usually recommended as the best for most people in terms of the features it offers and the ease with which anyone can make use of it. To get on the dark web, you need a browser built for the job, and the best in the business is Tor.
How KELA Cyber Supports You In Darknet Monitoring And Risk Mitigation
You can access the black market by navigating to the right “.onion” addresses. These sites are typically not listed on Google or other search engines. You can find them on private forums, message boards, and communities that work only by invitation. This is also a slippery road because many marketplaces get taken down by law enforcement or replaced by scam sites that can lead to malware or data leakage.
Versus Market (Best For User Reviews & Vendor Ratings)
Since the beginning of DWMs’ activity, there has been a shift in the law enforcement approach from focusing on market admins towards sellers and buyers9,13. For instance, a recent London Metropolitan Police (MET) investigation examined the transactions of a seller profile on a DWM10. The investigation uncovered a local criminal organization linked to a large international drug supply operation.
While these marketplaces continue to serve legitimate purposes, such as enabling secure communication and privacy protection, they also remain hotspots for illicit activities and cybercrime. Users must look for platforms employing robust encryption protocols, secure escrow services, and advanced anti-phishing measures. Additional layers, such as two-factor authentication (2FA), encrypted PGP messaging, and built-in wallet security, significantly enhance protection against theft and hacking.

Governments and businesses must invest in advanced threat intelligence, cyber defense, and counter-espionage measures. Dark markets include features similar to those found in legitimate e-commerce platforms, such as product listings, user reviews, ratings, and customer support. These features help create a sense of ‘trust’ among users, even in the criminal ecosystem. Dark markets, as well as various other services within darknets, are hosted as ‘hidden services’. This means that the servers providing these services are only accessible via Tor and do not have a public IP address or domain name.
Common Scams And Fraudulent Activities On Darknet Markets
The deep web is basically all the content that you can’t find using Google or Yahoo search. So, sites that contain a domain extension like .com, .org, .net, .biz, .info, etc. can be found on the surface web. In addition, the content on the pages don’t need any special or custom configuration to access.
This case demonstrates how proactive measures could significantly mitigate the risks posed by dark web activities. In 2021, a small marketing firm experienced a devastating data breach after employee login credentials were compromised and sold on a dark web marketplace. The stolen credentials allowed attackers to infiltrate the company’s email system, impersonate senior staff, and send fraudulent invoices to clients. Within days, the attackers had exfiltrated sensitive client information, including proprietary marketing plans and billing data. Yes, it often deals with illegal content for illicit purposes in a hidden part of the web called dark web.
Even people with little to no knowledge can buy ready-made ransomware and launch attacks on their victims. Once many users begin to rely on the site and store funds in escrow, the operators disappear, taking all the money with them and leaving their customers and clients with nothing. Imagine trusting a site where you’ve been buying or selling for months, and everything seems legit. Some marketplace operators first build trust by running a legitimate platform.



