
To get started, visit the official Tor Project website and download the browser for your operating system—Windows, macOS, Linux, or Android. Avoid downloading the browser from unofficial sources to prevent malware or tampered versions. Once installed, the browser is simple to launch, and it automatically connects to the Tor network.
- It organizes links to a wide variety of dark web destinations, including popular marketplaces where users buy and sell goods anonymously.
- For police, who would prefer criminals to face justice, this kind of exit causes mixed feelings.
- In addition to its main log-sharing function, Observer Cloud provides custom-built programs, a scam list, and chat groups for discussions and transactions related to logs.
- By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet.
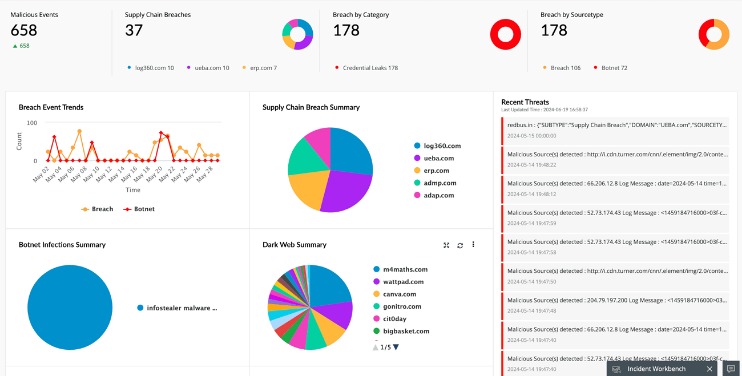
- From the data D3Labs has examined so far, about 30% appear to be fresh, so if this applies roughly to the entire dump, at least 350,000 cards would still be valid.
- By integrating these fraud detection mechanisms, businesses can reduce chargeback losses, prevent unauthorized transactions, and safeguard user data before it’s exploited.
“Rescator, which has ties to Russian-speaking actors, started operating again in December 2021,” Intel 471 says. It’s unclear if Rescator is operated by the same proprietor as before, or if its infrastructure was sold to a new operator, the researchers say, but credentials tied to the old site were valid on the new shop, suggesting a link. Depending on the virtual card provider, you can customize details like spending limits and even pause/close the card at your convenience. Credit card theft has become one of the most common types of fraud, with the U.S. projected to lose a staggering $165 billion in the coming 10 years due to card abuse. This integrated approach, combining insights from FraudAction and the protection of Outseer 3-D Secure, enhances fraud prevention, positioning the institution as a guardian of customer trust in the dynamic fraud landscape.
- Rapid response can prevent unauthorized transactions, minimize financial losses, and protect your customers’ trust in your business.
- At least 70% of the recorded calls supposedly include exploitable PII such as, first name, last name, registered address, phone number, e-mail, date of birth, card number, expiration date, and CVV.
- The Hidden Wiki is a gateway to these deep web resources, offering links to .onion sites that cannot be found via Google or other surface web search engines.
- Depending on the virtual card provider, you can customize details like spending limits and even pause/close the card at your convenience.
Russian Group Releases Stolen Credit Cards On Dark Web Here’s How To Protect Your Credit From Criminals
So unlike credit cards, prices for PayPal accounts and transfers have gone up during the pandemic by 293 percent. If you can, use an online wallet like Apple Pay or Google Pay, says Pascal Busnel, a director with ACA Group, a provider of risk, compliance and cyber solutions. This type of payment uses tokenization, which replaces your sensitive card data — like the expiration date and card verification value (CVV) — with a unique, random token.
The Dark Lair is another strong contender for those looking for dark web directories beyond the Hidden Wiki. It boasts a broad catalog of .onion sites categorized into marketplaces, forums, crypto services, and more. What sets The Dark Lair apart is its intuitive design and clear categorization, making it easier for new users to find reliable sites without getting overwhelmed. Additionally, it provides community ratings and user feedback, adding an extra layer of trust.
Understanding The Deep Web Vs Surface Web
This post will discuss deep and dark web credit card sites, specifically the top illicit credit card shops. The researchers at Cyble have estimated that over 20 percent of the credit cards are still valid. Therefore, consumers are urged to check their bank statements carefully for unknown transactions and contact their bank as soon as possible if there is any suspicious activity.
How War Impacts Cyber Insurance
Some vendors include access to a SOCKS5 internet proxy to help buyers avoid being blacklisted. Carders target sites without these protections, and some vendors even sell lists of “cardable” sites for a few dollars. These cards can be used to make purchases online or in-store, and can even be used to withdraw cash from ATMs. Although it monitors hacker forums, its coverage remains limited, as it does not track some of the key platforms listed in our Top 10 Dark Web Hacker Forums. The channel states that all shared content is sourced from open internet platforms and intended for educational purposes, disclaiming responsibility for any misuse of the published information.
Marketplaces: WhiteHouse Market, DarkMarket, Versus Market
Although it offers leaks from many different countries, the site has a dedicated lookup and leak section for Canadian profiles, making it extremely easy to use for buyers interested in Canadian leaks. All of these features, its competitive pricing, along with the volume of credit card information listings, make Real and Rare one of the prime sites to trade credit card information online. A Telegram channel specializing in the distribution of credentials obtained from stealer logs. With 20,000 members, Moon Cloud shares a wide range of compromised data, including URLs, email addresses, IP addresses, passwords, and usernames. Connect to the VPN before launching the Tor Browser, ensuring all your traffic is routed through the encrypted VPN tunnel first. Although this combination improves privacy, it can also further slow your connection speed, so balance your need for security with usability.
Frequently Asked Questions (FAQs) About Dark Web Marketplaces
They’ve essentially created a parallel economy with its own reputation systems, escrow services, and even customer support channels. Credit card fraud on the dark web operates quite differently from what many people imagine. This content creates an opportunity for a sponsor to provide insight and commentary from their point-of-view directly to the Threatpost audience. The Threatpost editorial team does not participate in the writing or editing of Sponsored Content.
More Hidden Sites

While the Hidden Wiki is a popular directory for accessing dark web resources, it is far from being completely safe by default. The dark web environment is notorious for hosting scam links, phishing clones, and honeypots designed to deceive visitors. Scam links may direct users to fraudulent marketplaces or services promising deals or products that never materialize, resulting in lost money or stolen credentials. Phishing clones are fake copies of legitimate dark web sites or marketplaces, created to harvest login details and personal information from unsuspecting users.
They can freeze the card and investigate further to trace usage details, suspicious activities, and other signs of theft. The stolen data reportedly includes a mix of credit and debit cards from major providers like Visa, MasterCard, American Express, and JCB. By observing how threat actors advertise and price different types of card data, we can identify which security measures they’re successfully bypassing and which ones are still effective.
The ProtonMail Onion site offers the same encrypted email services trusted globally, now accessible anonymously through Tor. This service protects messages from interception and censorship, critical for journalists and activists. Sigaint provides encrypted email favored by whistleblowers and privacy advocates, focusing on ease of use and robust security. For real-time messaging, Ricochet Refresh offers decentralized, peer-to-peer encrypted chats over Tor without central servers, greatly reducing surveillance risks. These services form the communication backbone for sensitive conversations in high-risk environments. These listings can include information such as the BIN number, credit card number, expiration date, and CVV number.


Many people seek it out for privacy and anonymity, as the Tor network and the Hidden Wiki help mask identities and activities from surveillance. The platform also supports freedom of expression by granting access to censored or restricted information, making it popular among activists, journalists, and individuals living under oppressive regimes. Furthermore, the Hidden Wiki plays a critical role in censorship resistance, providing uncensored content and services that might be blocked on the surface web. By implementing multi-layered identity verification, financial institutions can prevent fraudsters from using fullz to open fake accounts, apply for loans, or engage in other illicit activities.
WeTheNorth is a Canadian market established in 2021 that also serves international users. It offers counterfeit documents, financial fraud tools, hacking and malware services. Active for a decade since 2014, it is a widely used credit card shop used to source stolen credit card information such as dumps, CVVs, Wholesale Accounts. Some dark web marketplaces even host content that’s not just illegal but extremely harmful, so it’s really important to understand the risks before diving in.
While the Tor Browser provides strong anonymity, using a VPN (Virtual Private Network) alongside it adds an extra layer of security and privacy. A VPN encrypts your internet traffic before it enters the Tor network, hiding your Tor usage from your internet service provider and shielding your IP address from the first Tor relay. This setup can help prevent network-level surveillance and reduce risks in environments where Tor use might be flagged or restricted. Choose a trustworthy VPN service that has a strict no-logs policy and supports connection without DNS leaks. It comes just under a year since the retirement of the previous market leader Joker’s Stash, which facilitated the sale of nearly $400 million in stolen cards.
They use pseudonymous wallets, privacy coins (like Monero), mixers, chain-hopping, and non-KYC platforms to obscure transaction trails. There’s also a privacy angle—some users live in countries with censorship or surveillance, and the dark web gives them a space to communicate or access information more freely. In 2023, the dark web attracted an average of 2.7 million daily users, with Germany now leading as the country with the highest number of Tor users, surpassing the United States for the first time in years. According to Security.org’s 2021 Credit Card Fraud Report, users with enabled alerts were more successful in preventing money loss than those without.



