This is why many people prefer an identity theft protection service and a financial and credit fraud protection solution. By doing so, early signs of fraud can be detected in near-real time, such as new inquiries on your credit file like new credit cards or bank loans. However, while using Tor itself is not illegal, some illegal activities can occur through the network, such as the distribution of child pornography or the sale of illegal drugs. It’s important to note that engaging in illegal activities is still illegal, even through the Tor network. It is designed to provide online anonymity and privacy to its users.
Navigating The Dark Web Safely

Another standout feature is that the servers can’t see what you type, copy, paste, or send. To increase the security level, add password protection and determine the expiration time for messages. The Daniel site also had a status check feature that updated users on which sites were active. Unfortunately, the site’s admin could not keep up with the time demands and has taken down the links on the site as of August 2023.
The .onion site is aimed at individuals that want to share information anonymously with the spy agency but are at the risk of being tracked. It was created by the U.S Navy with the purpose of helping informants in foreign nations to communicate safely over the Internet. The Central Intelligence Agency (CIA), in that spirit, released a .onion site so that people from across the globe can browse their resources securely and anonymously.
Perplexity Offers $345bn For Google’s Chrome In Bid To Challenge Search Dominance

There are multiple search engines on the dark web that can help you find what you’re looking for. DuckDuckGo’s no-track dark web search service can be accessed in the Tor browser and is an excellent resource for information about the dark web. Other dark web search engines include Not Evil, Torch, Haystack, and Ahmia. You don’t need special tools or a special browser like you need to access the dark web (more about that later). Anyone can access the deep web by using specialized search engines, dedicated web directories, and other sources that can help you find the data or information.
Dangerous And Disturbing Services And Items
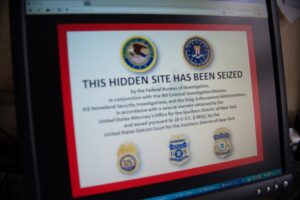
This can often be for political reasons, but also because they may be involved in illegal activities, such as the ones listed above. Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine. To access the dark web, you’ll need a specific set of tools – more about that later in the step-by-step section. Marques further admits that he willfully obstructed or impeded the administration of justice with respect to the investigation into this offense. You can buy almost anything on the dark web with Bitcoin and other cryptocurrencies, from secondhand furniture to illegal drugs, porn, exotic animals, and all manner of criminal services-for-hire. The internet’s favorite alternative to Google made a name for itself by not logging your search activity yet still providing decent results.
- Simply put, accessing and browsing the dark web is perfectly legal.
- It hosted approximately 91,000 unique videos, amounting to nearly 6,288 hours of explicit content—all shared on a highly profitable network.
- Then there’s the less popular VPN over Tor, which is advised against by the official Tor Project.
- If you wish to access the snapshots of these websites, just type in the domain name, and you will get the results depending on how many records exist on the website.
- Different dark web search engines cater to various needs, offering varying levels of privacy, security, and ease of use.
Commercial Services
Fraudulent activities on the dark web include phishing scams, fake identity sales, and the sale of fake products. Counterfeiting businesses create fake versions of popular products and sell them on the dark web. Bitcoin allows for anonymous donations, making it easier for terrorists to fund their activities and purchase weaponry.
Starting with ProPrivacy and now Proton, Douglas has worked for many years as a technology writer. During this time, he has established himself as a thought leader specializing in online privacy. Douglas was invited by the EFF to help host a livestream session in support of net neutrality. At Proton, Douglas continues to explore his passion for privacy and all things VPN.
This adds another, more reliable security layer to all of your online activity. Viruses, ransomware, and other types of malware are more common on onion sites than on the normal internet. Many pages have poor encryption standards and no other protections, so simply visiting a Tor site can infect your device. Ahmia also discourages access to illegal content and promotes safer internet practices.
Facebook Onion Site
The problem is that getting to those forums may require opening yourself up to safety concerns like the ones listed above. Even in an era of increased online surveillance, the average person on the internet likely has too much to lose to bet on their safety for curiosity’s sake. Heck, I’m one of PCMag’s resident security experts, and I’m not playing around on the dark web just because I know how to. That’s why I’m not going to provide links or detailed instructions for accessing the internet’s shadier side.
Over the past three years, the site amassed around 1.8 million users worldwide. It hosted approximately 91,000 unique videos, amounting to nearly 6,288 hours of explicit content—all shared on a highly profitable network. Kidflix was a dark web streaming platform that provided access to thousands of videos depicting extreme child sexual abuse—including crimes against very young children. If you stumble upon illegal content or believe you’ve become a victim of a scam, it’s important to report it to the appropriate authorities, just as you would in the physical world. Always connect through a VPN like Forest VPN to encrypt your connection and protect your identity.
SecureDrop — Secure File Sharing For NGOs, Journalists & News Organizations
The final relay before your traffic goes to the destination website is known as the exit node. The exit node decrypts your traffic and thus can steal your personal information or inject malicious code. Additionally, Tor exit nodes are often blocked by websites that don’t trust them, and Tor over VPN can’t do anything about that, either. That information is hidden simply because most users won’t find it relevant.

While they might sound the same, these websites are fundamentally different. Read about the adventures of modern-day explorers who have made it their mission to venture into the tunnel network of huge American universities. The site is different from our whole list, but still worth a mention. Still, while the latter has a large digital collection of comic books, the Imperial Library has a large collection of books.
More On How To Stay Safe On The Dark Web
The site also uses strong encryption to protect against cyberattackers, such as anti-DDoS protection. It doesn’t use JavaScript, which goes a long way toward keeping you anonymous. When you access this site, do so with extra protection, even if you are technically anonymous when you use the Tor browser. We highly recommend using a strong VPN like NordVPN to stay safe and private.
Services like Random Chat connects you with random people using the same service. If the signal goes through the Tor network first, your ISP will be able to see that you are attempting to connect to a Tor node. Though no one should bat an eye just because you’re attempting to access the dark web, keep in mind that in some countries, like the United States, even a simple foray can get you in trouble. It makes up about 6% of the internet, and it’s where you find everything from illegal marketplaces to forums for whistleblowers. If you’ve ever checked your medical results online through a portal that required a login, you were navigating the deep web. It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security.
Latest Crime News
Among those detained were not only consumers of the illegal content but also direct perpetrators of abuse. Besides offering a secure connection, Forest VPN is designed to use less battery, reducing your carbon footprint. Its competitive pricing ensures that robust privacy protection is as affordable as a cup of coffee. Plus, with no logs or data collection, your activities remain your own secret. And in 2017 the company announced a switch to HTTPS as part of a major security upgrade against hackers and malware. Visiting onion sites on older Tor versions can needlessly expose you to added risks.