You can also consider using a credit monitoring service to alert you to any changes in your credit report. Staying vigilant and proactive can minimize your risk of falling victim to credit card fraud. Regularly monitor your accounts, use secure connections and invest in tools like credit monitoring services for additional peace of mind.
NodeBB Vulnerability Let Attackers Inject Boolean-Based Blind And PostgreSQL Error-Based Payloads
A security researcher, Kasra Rahjerdi, discovered the messages while investigating the app’s data security. He stated that while Tea’s own API had strong protections, its use of Firebase to store data created vulnerabilities that allowed access to real-time private communications until July 26, 2025. Although Workday did not directly name the group, security researchers linked the incident to ShinyHunters, which has run similar attacks against major companies including Adidas, Qantas, Allianz Life, Dior, Chanel, and Google.
Massive Data Google & Apple Breach Exposes 184 Million Passwords
In July 2024, the hacker group SiegedSec claimed responsibility for breaching the Heritage Foundation, a conservative think tank. The group released internal communications and documents, alleging the breach was in protest against the organization’s political activities. Between June and August 2024, Japanese publisher Kadokawa and its video-sharing platform Niconico suffered a ransomware attack by the Russian-linked hacker group BlackSuit. One of the main challenges has been inconsistent cooperation across crypto platforms. The exchange eXch allowed over $90 million to be moved through its systems before taking action. While ByBit’s CEO Ben Zhou emphasized that no customer funds were affected and the firm has replenished the stolen amount through investor loans, the company launched a Lazarus Bounty program.
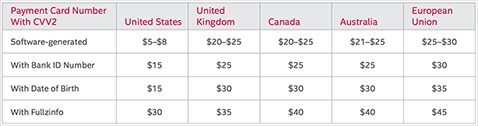
By using specialized tools cybersecurity professionals can track these illegal activities and alert financial institutions of potential threats. This article will explore credit card theft on the dark web, explain how criminals obtain and use stolen data, and explain how to detect and prevent credit card fraud. These aren’t just random forums, they’re organized platforms where stolen card data gets packaged and sold as “fullz” (full card details including CVV) or “dumps” (raw magnetic stripe data). Leaked credit cards from Telegram channels account for the overwhelming majority of compromised payment card details. At the time of this publication, the marketplace holds an inventory of over 2,749,336 credit cards, with an average price per card of $US 6.
Holt Group And Associated Businesses Breach

Since late May 2021, the threat actor has been actively advertising and promoting the new platform on different Dark Web hacking-related platforms. The current leak of one million credit cards by the threat actor appears to be another marketing move to attract potential clients from hacking and cybercrime forums and increase the platform’s popularity. Modern credit card fraudsters rely on specialized software frameworks to automate their operations.

Content strives to be of the highest quality, objective and non-commercial. While SSN, name, and DOB are all fairly standard in fullz, other information can be included or excluded and thereby change the price. Fullz that come with a driver’s license number, bank account statement, or utility bill will be worth more than those without, for example.

Understanding Credit Card Fraud On The Dark Web
The key is catching this activity before large volumes of card data make it to market. This enables systems to detect fraud based on minute changes in transaction velocity, merchant category patterns, and even the time of day purchases are made. Financial institutions tighten their security measures to prevent fraud but that also prevents legitimate transactions as a result.
- There are of course many ways to skin this proverbial feline, but it can be illuminating (possibly concerning) to see the actual steps involved.
- The first breach occurred in April 2022 when a former employee accessed sensitive data on over 8 million users.
- The source of the payment card batch, which went on sale on the Joker’s Stash on Wednesday (February 5), remains unconfirmed, although circumstantial evidence suggests it came from online theft.
- What makes these tools particularly concerning is their accessibility.
- It can take months—or even years—to recover from this kind of identity fraud.
Most of use just have the standard personal account, but Premier and Business accounts also exist, and are up for sale on the dark web. But those tiers don’t have much influence on dark web prices, which are largely governed by account balance. In a similar study earlier this year, we noted an average price of 3.13 cents per dollar in the account. So unlike credit cards, prices for PayPal accounts and transfers have gone up during the pandemic by 293 percent.
NationsBenefits Holdings Data Leak
You may have never been to the dark web — but there’s a chance your credit card information has. This tactic mirrors similar marketing stunts by other illicit platforms, such as BidenCash, which leaked 2 million cards in 2024 to celebrate its anniversary. The pausing/closing feature is especially useful if a specific Privacy Card has been exposed in a data breach or you want to block hidden/unwanted subscription charges.
Over 30 Million Stolen Credit Card Records Being Sold On The Dark Web
The incident, disclosed in its Q3 earnings report, continues to disrupt fulfillment and supply operations. Mador recommends that merchants carry out penetration testing, via a third-party security company, to scan websites and applications on an ongoing basis. “We report when we see security issues—missing patches, nonsupported software, or using out-of-date versions of programs,” and then recommend steps for remediation. VPN access credentials were the most expensive category of data that SpiderLabs found being sold on the dark web. Ensure that your transactions comply with relevant data protection laws which aim to secure personal information from misuse.
Compliance With Data Protection Laws
The process, also called skimming, allows them to make physical purchases at ATMs or retail stores. Unlike online fraud, this type of theft is harder to detect because the transaction appears as a regular swipe. The IMF responded by securing the accounts, enforcing multi-factor authentication, and boosting employee cyber awareness. This cyber incident joins the list of latest data breaches that show how a single point of failure can threaten sensitive data.
These cards can be used to make purchases online or in-store, and can even be used to withdraw cash from ATMs. This extra layer of security gives peace of mind in today’s digital world. With just a few taps, people can see exactly where their money goes and catch problems early.
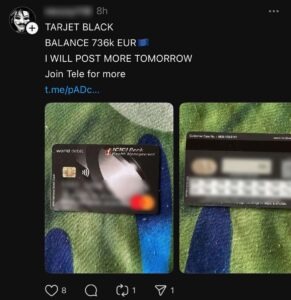
Telegram Carding Groups
By clicking “Continue” I agree to receive newsletters and promotions from Money and its partners. I agree to Money’s Terms of Use and Privacy Notice and consent to the processing of my personal information. One of the largest known underground shops, Joker’s Stash, generated more than $1 billion before getting shut down in February, according to Gemini Advisory. A 2019 data leak of another shop, BriansClub — which appears to have been by a competitor, according to Threatpost —shows how pervasive this trend has become. He said it felt more like a “victimless crime” because he thought most people would end up getting their money back anyway. Depending on the virtual card provider, you can customize details like spending limits and even pause/close the card at your convenience.