
It is one of the most active and up to date markets and always provides new and updated malware and data. Torzon Market has established itself as a significant player in the darknet ecosystem, offering a secure, user-centric platform for anonymous trading. Its commitment to privacy, diverse product offerings, and robust security measures make it a preferred choice for users seeking discreet transactions within the darknet.
Be sure that your experience with Whonix will be comparable to Tor because both programs share the same source code. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web.
Disk encryption is also recommended in order to deal with ransomware problems. Methodologies for disk encryption that are easy to understand are accessible on the Internet. In the dark web, certain of the most dangerous key loggers and phishers are functional. An established method of holding hackers at bay is to install an operating system like Linux. It helps to hide real internet address during surfing dark web links.
Is It Legal To Access Dark Websites?
These sites aren’t accessible via standard web browsers or search engines. The dark web contains content that’s only accessible through networks like Tor. Tor browsers create encrypted entry points and pathways for the user, so dark web activity remains anonymous. The encryption technology routes users’ data through a large number of intermediate servers, which protects the users’ identity and guarantees anonymity.

Maltego + Darknet Plugins

It’s an easy and simple way to de-couple your internet usage from Google’s monopoly over the web. Always run the latest version of the Tor Browser to protect against security vulnerabilities. Outdated versions may contain weaknesses that attackers can exploit to compromise your anonymity. I recommend enabling automatic updates and checking for new versions before each session. The keyword in that example is “onioname,” which is right at the start of the .onion link. With a readable site name like that, people will know what to expect when they click on the link.
Best Dark Web Websites: Video
It delivers an uncensored search experience, granting users access to a diverse array of information while effectively excluding illegal content. Dark web search engines are an alternative to having high technical knowledge, something hackers, journalists, and security firms are used to. With a single click of a button and going through some web pages, one can now easily visit a dark web page. It is that hidden corner of the internet that is hidden from the public and can only be used by a limited number of people. Hackers, journalists, and security companies use this hidden corner to exchange information and gather intelligence that’s not accessible through the regular internet.
Dark web domains are generated in a cryptographically secure way, so they look like random strings of 16 characters or more (like 3g2upl4pq6kufc4m.onion, for example). For example, I looked up google.com and was able to find a snapshot of Google’s home page from 2008. The Mail Plus plan adds up to 15 GB of storage, unlimited messages, and 10 email addresses, plus advanced email settings (like automatic forwarding). You can also get Proton Unlimited and Proton Duo plans that add even more extras. ProPublica exposes corruption and abuses of power through investigative journalism.
Wherever you are online, make sure you have trusted software protection to help keep you safer from the not-so-mythical cyber-monsters and online threats lurking there. The Tor Onion Browser is essential for accessing the dark web, designed for user anonymity. Unlike the regular internet, the dark web doesn’t use standard URLs or search engines.
Hidden Wallet
The articles are in-depth and informative, and the site is completely free to access — no random paywalls pop up in the middle of articles. Info like your name or email address never needs to be shared on the dark web. You should also limit the number of financial transactions you make on Tor banking portals. Enable MFA wherever possible to protect your accounts from unauthorized access. ZeroBin encrypts any text pasted into it, and its own servers don’t even know what you pasted.
Facebook’s onion Service
In this article, we look at some of the best legitimate Tor websites on the dark web. Explore how cryptocurrencies enable secure, anonymous transactions in the digital age. Make Tech Easier provides tech tutorials, reviews, tips and tricks to help you navigate the complicated world of technology. Never log in with your real name or reuse passwords from other accounts. Stick to cryptocurrency, avoid downloading anything, and don’t share any personal info. Some markets are invite-only or have strict registration rules to keep out scammers and law enforcement.
- The Internet is a vast and complex landscape, much larger than the familiar interface we use every day.
- Dark web domains are generated in a cryptographically secure way, so they look like random strings of 16 characters or more (like 3g2upl4pq6kufc4m.onion, for example).
- Installation of a specific browser package is required to browse dark web links.
- There are also many tools that can be use to monitor the dark web and scan for personally identifiable information and even respond to attacks.
- Today, this witch is one of the few ways to access onion websites located on the web.
- But despite its many benefits, it’s sadly just a matter of fact that the dark web can be a dangerous place.
Why People Use The Hidden Wiki
Unlike the surface web, which is indexed by mainstream search engines like Google and Bing, the dark web remains largely out of sight, only accessible using specialized tools and browsers. This hidden realm attracts legitimate users, such as journalists and whistleblowers. However, it also appeals to those with more nefarious intentions, like cybercriminals and fraudsters. The Dark Web is just a collection of websites not listed by regular search engines like Google or Bing. Users cannot visit .onion sites using normal browsers like Chrome, Firefox, or Edge.
Our commitment to delivering top – notch, engaging, and business – centric content is what sets us apart. We aim to be the go – to destination for industry – leading news, in – depth analysis, and practical advice. Navigating the vast expanse of the internet, the best Tor websites emerge as sanctuaries of privacy, security, and freedom. To access the Tor network and the best Tor websites, you’ll need the Tor Browser, which is specifically designed to navigate the Tor network. It’s essential to exercise caution and conduct thorough research before accessing any website on the Tor network. While they have gained notoriety for the sale of banned substances and illegal goods, many markets focus solely on legal products.
Why Choose Forest VPN For Dark Web Exploration?
DuckDuckGo’s approach to search is built on the premise that personal information should remain private and that users should not be profiled based on their search queries. Because the Hidden Wiki aggregates many links, it often contains outdated or malicious URLs disguised as legitimate ones. This makes blindly clicking links risky and requires users to exercise caution when navigating these directories. Be mindful that not all content on the dark web is legal or safe; avoid engaging with illicit activities or sites promoting harmful behavior. Lastly, consider using a trusted security tool or firewall on your device and stay informed about the latest dark web threats through reliable sources.
Can You Be Traced On Tor?
There are a variety of private and encrypted email services, instructions for installing an anonymous operating system and advanced tips for the privacy-conscious. Dark web search engines exist, but even the best are challenged to keep up with the constantly shifting landscape. The experience is reminiscent of searching the web in the late 1990s. Even one of the best search engines, called Grams, returns results that are repetitive and often irrelevant to the query. Link lists like The Hidden Wiki are another option, but even indices also return a frustrating number of timed-out connections and 404 errors.
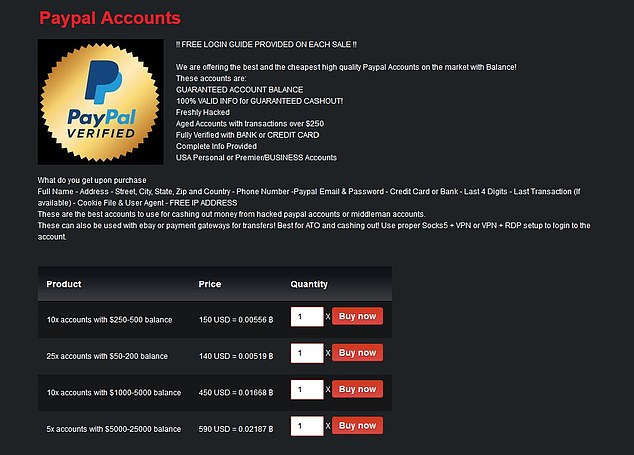
Popular news publications like The Washington Post, The Guardian, TechCrunch, and more have set up their own SecureDrop URLs so whistleblowers can contact them effortlessly. SecureDrop claims that all the messages you send and receive are encrypted in transit to prevent third parties from intercepting them. One of its journalists, Hannah Dreier, won the 2019 Pulitzer Prize for Feature Writing for her coverage of gangs in Los Angeles. You can access Facebook via the dark web by using the official Facebook .onion mirror. Even completing a transaction is no guarantee that the goods will arrive. Many need to cross international borders, and customs officials are cracking down on suspicious packages.



