Pirate Bay, a BitTorrent site that law enforcement officials have repeatedly shut down, is alive and well there. We don’t want to leave you with the impression that everything on the dark web is nefarious or illegal. The Tor network began as an anonymous communications channel, and it still serves a valuable purpose in helping people communicate in environments that are hostile to free speech. “A lot of people use it in countries where there’s eavesdropping or where internet access is criminalized,” Tiquet said.

Forest VPN: Your Gateway To Safe Browsing
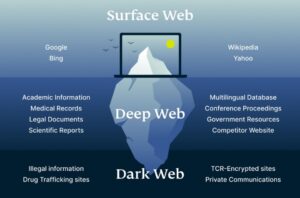
Always remain cautious, respect the law, and enjoy the wealth of resources the dark web has to offer. From drug trafficking to arms deals to stolen data, the dark web provides a marketplace for many illegal goods and services. This has led to a negative reputation and is attracting the attention of law enforcement agencies. If one tries to visit the dark web with a regular browser, there will be no web pages to visit. Since the dark web is hidden from the surface web, these dark web search engines allow users to explore the concealed part of the Internet. The dark web is home to the internet’s hidden sites, services, and products — some innocent, others downright dangerous.
Furthermore, the service does not require user registration, allowing anyone to archive and access snapshots anonymously. Established as part of the Tor Project, Tor Metrics aims to quantify the network’s health, performance, and reliability. This information is invaluable for developers, researchers, and users interested in the technical and sociological aspects of the Tor network.
Browse The Web More Safely
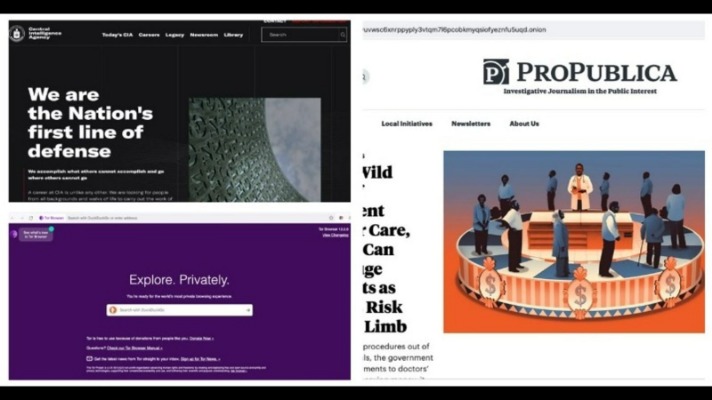
The CIA is contactable on the dark web, providing a completely anonymous way to get in touch with them. However, if you’re communicating with state intelligence agencies, you should use Tor alongside a VPN for maximum privacy. Otherwise, the first node in the onion relay system sees your real IP address, which can be used to locate you and unveil your identity. While no single tactic is foolproof, a layered approach—combining technical, operational, and psychological defenses—greatly improves your safety and confidence when navigating the dark web.
Dangerous And Disturbing Services And Items
You should also keep in mind that overall speeds will likely be impacted; for example, a page might take a few seconds longer to load than what you are used to. A VPN and Tor should be used together and it is advisable to connect via a VPN to Tor, rather than vice versa, for the best protection possible. If you need to access dark web resources, these are the steps you need to take. The dark web, however, requires special software to access, as explained below.

Get Out Of The Audit Committee: Why CISOs Need Dedicated Board Time
You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe. Alt Address provides disposable email addresses specifically designed for dark web use. This service helps protect your primary email when signing up for .onion services. I found it especially useful for testing new services without risking my main email address, though messages expire after 24 hours. But despite its many benefits, it’s sadly just a matter of fact that the dark web can be a dangerous place.

Step 1: Download And Install The Tor Browser
Using a reliable VPN provider helps keep you safe when you access marketplaces on the dark web. A VPN encrypts the data traffic and keeps your activities private on the dark web. It also masks your IP address, making it difficult for government agencies to monitor or track your activities. We recommend using NordVPN as it offers top-notch security features, including dark web threat protection. The dark web is a hidden part of the internet where users are anonymous and can access illegal marketplaces and hacking forums and partake in illicit activities.
Media Outlets With A Secret Door
- The most common way to explore the dark web is through the Tor browser, which anonymizes users by routing their connection through multiple servers before reaching the intended site.
- DuckDuckGo’s dark web version offers the same privacy-focused search experience as its clear web counterpart.
- I possess a keen interest in exploring and understanding the intricacies of malware, Advanced Persistent Threats (APTs), and various cybersecurity challenges.
- Launched in the early 2010s, Archive Today’s primary mission is to combat the transient nature of the internet, where web content can change, disappear, or be altered without notice.
- On the Tor network, the onion domain name reflects the fact that, like the layers of an onion, the Tor browser consists of layers of protection.
To look at it in a different way, it makes up between 90% and 95% of the internet. In addition to the Tor browser, you should use an antivirus program (like Norton 360) to protect your device from malware infections, and a VPN (like ExpressVPN) to secure your IP address and traffic. Also, only use .onion links from legitimate sources like The Hidden Wiki.
Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny. The US Supreme Court has indicated that even casual browsing could lead to legal consequences. Whether you’re curious about the hidden corners of the internet or need practical tips on navigating it, we are here for you. Even with these legitimate offerings, the dark web is not without its risks. Always verify the legitimacy of a site before sharing any personal information. Yes, many professionals use tools like Maltego, IntelX, and custom scripts to automate scraping, indexing, and alerting on dark web activity.
- These search engines neither track your search queries nor record any information, improving digital privacy and keeping your data private.
- Since the organization behind it is independent, it’s fully user-supported and relies on donations to keep its site up and running.
- I found in my tests that all features work identically to the regular version.
- Its intuitive interface and advanced search features make it easy to find local and global products.
The entire website is in Russian, but the vendors are present worldwide. It accepts payments through Bitcoin and the Escrow system and ensures that your identity remains anonymous during your purchases. Vice City Market is a new and cutting-edge dark web marketplace where you can find a range of products and vendors at an affordable price (compared to the damage they do to the victims). To access this marketplace, you must register, but before that, you must verify yourself as a human by passing a CAPTCHA test.
Tor Metrics
These search engines work best if you already know what site you’re looking for, not for general browsing. Blockchain.info (now Blockchain.com) is a popular cryptocurrency wallet and blockchain explorer service (one of the first sites to launch on the dark web). It was initially created to provide additional security and eliminate cryptocurrency theft. It’s a wallet, explorer service, not a dark web marketplace itself, but still a helpful resource. Established in 2012, the platform is a time capsule that collects snapshots of websites.
Overflow: Hidden;
Sure, you can use other cryptocurrencies if Bitcoin’s not your cup of tea. You should stay away from everything labeled “porn”, “card skimming services”, “PayPal hacks”, “firearms”, “real fake IDs and passports”. Believe me – there are plenty to go around and each and every one of them are being kept under surveillance. Not to mention the fact that you’ll get exposed to some stuff that will definitely make you take several cold showers. At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen.
While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web. No one is hiding here—they’re just guaranteeing that people in censored countries can read the news without being flagged. There are often copious amounts of how-to articles, software exploits, and hacked credentials for sale. Not every visitor is a criminal, but this is where most cybercrimes begin. These are the primary sources of what the general public thinks of as “dark web.” Online marketplaces selling hacked credit cards, fake passports, malware kits, untraceable drugs, anything.