The history of the Dark Web is intricately tied to the development of internet technology and the ongoing pursuit of online anonymity. The concept of an encrypted, hidden layer of the internet began taking shape in the 1990s. The U.S. Naval Research Laboratory developed the precursor to the Tor (The Onion Router) project during this period as a means to protect government communications. The dark web is notorious for hosting a wide range of cyber threats that pose significant risks to individuals and organizations. One common threat is the sale of stolen credentials, including usernames, passwords, and financial information, which cybercriminals use for identity theft and fraud. If you want to be extra safe, routing your connection through a VPN and then accessing the dark web using the Tor browser provides more security than Tor alone.
Check around with other users and ask if they know anything about the new marketplace. I2P can only be used to access hidden sites that are only available on the I2P network. As I mentioned previously, the dark web is quite popular with journalists, political bloggers and news publishers, and others who run the risk of imprisonment in countries like Iran and others. Supreme Court will allow the FBI to search and seize any computer that’s using the Tor browser or VPN. Rule No.41 allows a federal judge to issue a search and seize warrant for any person who is using anonymity software like Tor.
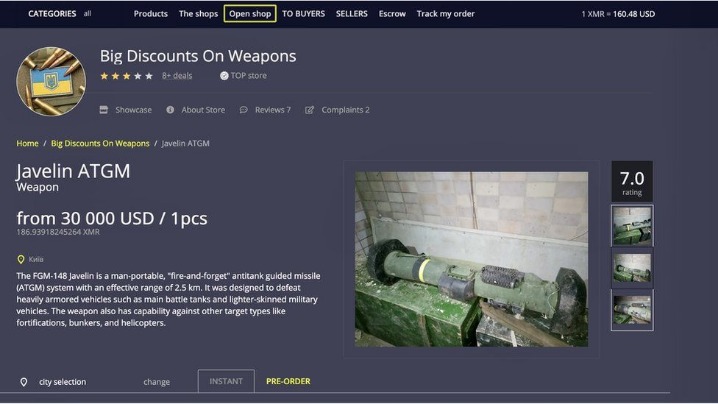
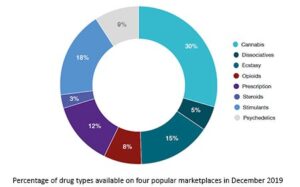
Many people see hacked information and stolen card data being sold on the dark web. For example, you can find information unavailable to the public and share data privately while protecting your online identity. Note that most dark web transactions are carried out using Bitcoin or other cryptocurrencies. However, there’s a chance you may run into illegal activity on all but the best onion sites. Most internet users want to use the dark web safely, but it’s still important to be careful when using any onion browser. On the other hand, the dark web hosts marketplaces and forums where illegal goods and services—such as drugs, weapons, and stolen data—are traded, making it a hotspot for criminal activity.
Slide up to the “safest” level, and as well as those settings, JavaScript is disabled on all sites. If your Social Security number is found on the dark web, take immediate action to protect yourself. Place a credit freeze or lock on your credit reports, monitor your credit reports and financial accounts closely for any unauthorized activity, and consider enrolling in a credit monitoring service. Additionally, contact the Social Security Administration to report the breach and discuss further protective measures. This is in part a response to exit scams, such as what AlphV/BlackCat and other marketplaces have pulled.
It’s a hidden collective of sites that you could only access through a special browser. Since all activity on the dark web is anonymous by default, it is definitely where the murkiest transactions on the internet take place. A study by researchers at King’s College London that examined the contents of over 2,700 darknet sites found that approximately 60% of them hosted illicit content. The deep web is the part of the internet you can’t access through search engines like Google and Bing. Also referred to as “non-indexed” content, it’s any content hidden behind some kind of access control such as a log-in or code word.
What Are The Limitations To Onion Routing And Tor?
In addition, Haystak offers a premium plan that allows deeper search, email alerts, and access to historical content. For individuals in locations facing strict restrictions or those under oppressive governments, ProPublica is the perfect platform to share their stories. ProPublica aims to bring controversial, repressed stories into the open for all to see. It publishes news in English and other major languages like Italian and Spanish.
Data Breach Detection & Response
One of the primary techniques used to gather data from the dark web is web crawling and scraping. Unlike the clear web, search engines don’t index dark web sites, making them hard to locate. Advanced web crawlers are used to automate the process of discovering and collecting data from these hidden sites. The “dark web” consists of hidden websites that you can’t access without special software. These websites won’t appear when you use Google or another search engine, and you can’t even access them unless you go out of your way to use the appropriate tools.
- A VPN protects your connection against everyone, not just your ISP and the authorities.
- This platform allows visitors to anonymously explore the World Factbook, submit information, apply for jobs, and perform any other actions available on the CIA’s main site.
- Near total anonymity and a complete lack of regulation can easily attract criminality, and onion sites can harbor malware such as ransomware or spyware.
- It also keeps the graphical copy and text of the page for better accuracy.
- This double encryption also protects against compromised Tor entry nodes that could potentially monitor your activity.
- After all, it enables users to connect and communicate with each other from around the world.
What Is The Best Dark Web Search Engine?
There’s a reason why this onion website is called the Imperial Library; with over downloadable 500,000 books and articles, this may be one of the largest digital libraries, period. As I’ve previously said, it’s a good idea to keep your interactions with the dark web to a minimum, unless you can absolutely trust the people you’re dealing with. You’ll often see a sign in stores that says “look, don’t touch,” and it’s not a bad adage to bear in mind as you navigate around the dark web. For obvious reasons—I don’t want to get you or me into trouble, after all—I’m not going to get too specific when it comes to what you can find for sale on the dark web.
The Hidden Pitfalls Of Travel Apps
Increasingly, privacy-focused coins such as Monero (XMR) and Zcash (ZEC) are being adopted to protect anonymity and make tracing funds difficult for law enforcement. ESentire’s Threat Response Unit has also observed AI integrated into the StealC admin panel to help filter stolen logs. There are also reports of “evil GPT” products sold on dark forums or via private messaging, according to Vishavjit Singh, senior threat intelligence researcher at eSentire.
Examples Of Dark Web Resources
The famous social media platform has a prominent presence on the dark web. However, we do not advise readers to log onto this dark web mirror site; doing so would risk their privacy and that of others. If we need a website to get links to other hidden sites, we will choose Hidden Wiki. But if you are thinking you can find links to the deepest part of the dark web using this site, it’s not that simple.
You can also use the Tails operating system to further protect yourself. If you’re just browsing the dark web out of curiosity, Tor, or a Tor and VPN configuration is safe enough. If you’re trying to hide from an oppressive government or want to be a whistle-blower for something illegal, take as many steps as you can to be safe.
Facebook — Dark Web Version Of Popular Social Media Site
Cryptocurrency, particularly Bitcoin, plays a significant role on the Dark Web. Many transactions conducted on the Dark Web involve the exchange of cryptocurrencies, as they offer a level of anonymity that traditional currencies cannot. For example, the Freedom of Information Foundation has long advocated for the use of the Dark Web in enabling free speech in repressive regimes. By offering secure communication channels, it gives people in oppressive states the opportunity to connect with the outside world and engage in activism without facing the consequences of being identified. The most notorious marketplace to date was Silk Road, an online black market for drugs, which was shut down by the FBI in 2013.
It does not store logs and is protected from interference and malicious attacks. The platform is free and is run by volunteers in the US who prefer privacy and security. The platform utilizes end-to-end encryption, ensuring it does not store any activity records. Like other email clients on the dark web, it does not require you to give your personal information. It is a Swiss-based company (privacy-friendly country), and all its tools are open-source, meaning anyone can test its vulnerabilities.
Tor Links is a backup directory of “.onion” sites in case other directories go offline. The best Tor sites are under constant threat of closure, including Tor directories like the Hidden Wiki, so having a backup in case one goes down is handy. ZLibrary hosts free file-sharing access to academic texts, scholarly articles, and general-interest books. It often hosts copyrighted materials without permission, violating many countries’ copyright laws.

If you’re unsure about the legal boundaries in your country, consulting a knowledgeable attorney or reviewing reputable sources of legal information is a prudent first step. DuckDuckGo is a privacy-focused search engine that works as Tor browser’s primary search engine. It doesn’t track searches or store personal data, making it a strong option for users seeking more anonymous private browsing.