That’s why the cybercriminals use these forums, as they know that they’re there to stay. Additionally, cybercriminals use these forums as they offer stolen data. Perhaps one of the major attraction factors of these forums is undoubtedly anonymity. Cybercriminals want to carry out their illegal activities without detection by law enforcement agencies and other authorities.
What Is The Dark Web? How To Access It Safely?
Furthermore, it’s critical to understand that Whonix is not a stand-alone browser. It is a component of Whonix, an operating system that functions as a whole inside a virtual computer. It includes all the essential productivity software, including MS Word and an email client. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web.
Dark Web Links: The Onion Patch – Best 20 Websites You Shouldn’t Miss
- In due course, the framework was remodeled and made public as a secure browser.
- If the websites you visit use tracking scripts, third parties can monitor you.
- The story of dark web marketplaces kicks off with Silk Road, launched in 2011.
- Rule No.41 allows a federal judge to issue a search and seize warrant for any person who is using anonymity software like Tor.
- However, it’s much harder to get at the people who are doing the uploading and downloading.
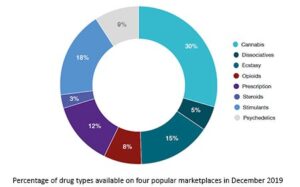
Some of the reasons why it’s worth monitoring these hack forums include, ability to detect breaches early, gaining threat actor insights, and third-party risk mitigation. If you’re a company, you might want to monitor the dark web to safeguard your reputation and compliance. If you can find your data even before attackers exploit it can help you prevent PR disasters. It’s known that the best place to purchase or even exchange various hacking tools is on the dark web discussion boards. In these forums, you can get stuff like malware, hacking tools, and exploits.
- These layers upon layers give this network its iconic “onion” name—as the onion itself has layers upon layers.
- Naturally, this makes the dark web a breeding ground for illegal activity.
- It’s committed to transparency and public service, which is why it maintains a dark website along with its site on the surface web.
- ExpressVPN is an excellent choice for Tor and accessing the Dark Web.
- If you’re a company, you might want to monitor the dark web to safeguard your reputation and compliance.
OnionShare
This is a great resource for users looking to refer to old prices or job listings that have changed or are outdated. Accessing tunnels is illegal and dangerous, which is why records of these “adventures” can only be found on the dark web. If you want to access this site, do it only for fair purposes and with proper security measures.

Onionname
The Tor Metrics is a good place to get more information about the Tor project. It collects data from the public Tor network and archives historical data of the Tor ecosystem. ProPublica is a popular online publication that won five Pulitzers in 2016. It aims to expose abuses of power and betrayal of public trust through investigative journalism.

Marketplaces
Accessing them may require .onion links and the Tor browser, but caution is advised due to legality and cybersecurity risks. WeTheNorth is a Canadian market established in 2021 that also serves international users. It offers counterfeit documents, financial fraud tools, hacking and malware services.
Tor offers secure and encrypted access to the dark web forums, ensuring that the user’s IP address is hidden and difficult to trace. Therefore, cybercriminals use these forums because they offer assured anonymity and security. Naturally, this makes the dark web a breeding ground for illegal activity. But onion sites can also serve nobler goals, like providing access to information and independent journalism in countries with government censorship. The deep web is the part of the internet you can’t access through search engines like Google and Bing. Also referred to as “non-indexed” content, it’s any content hidden behind some kind of access control such as a log-in or code word.

Where Should I Explore The Dark Web? And How Can I Know If Websites Are Safe Or Not?
Onion.name is a dark web resource that helps make sense of the mess of letters and symbols that usually form the darknet sites. This tool rewrites dark websites into easily understandable texts. However, we do not recommend using this platform without taking proper precautions, such as anti-malware and a VPN. You can also use it on the surface web, but it is still unadvisable without proper safety measures. To provide freedom of speech and keep journalism a strong pillar of the economy, the BBC made this Tor mirror. It helps people anonymously use the BBC website without restrictions.
It’s maintained by an independent organization committed to digital privacy and security. It runs an onion site to help like-minded people mobilize more securely and anonymously. But while anonymous email services can help protect your identity, they don’t make you immune to threats like email spoofing or social engineering. And it’s still essential to use strong passwords and two-factor authentication (2FA) to help keep your account secure. Crypto services use various measures to keep cryptocurrency wallets secure and make sure your Bitcoin is safe. Some, such as Wasabi Wallet, provide an extra layer of security by using onion routing to pass crypto activity through multiple nodes, none of which know the sending and receiving IP addresses.

Prominent organizations like The Guardian, The New York Times, and ProPublica have implemented it. The software requires two-factor authentication to receive what’s been uploaded by the whistleblower and allows two-way communication between the anonymous contact and the media outlet. Although profiting from pirated copyrighted material is unethical and illegal, there are some exceptions to using copyrighted material, such as a “private study” provision under UK law. Of course, bypassing paywalls is ethically questionable and may be illegal in some jurisdictions. That’s why many people choose to do so anonymously on the dark web, rather than using the clear web version of the site.
This confusion is understandable, giving the different explanations that are on the internet. So I’ll do my best to clear these confusions up by giving my best shot at explaining the differences the way I understand them. Qubes is used by journalists, as it is directly used to run SecureDrop, another dark web website on our list.

Malicious actors can prey on unsuspecting users without leaving much of a digital footprint on Tor, so it’s often just a matter of time before you run into one. ZeroBin is a minimalist paste-bin tool that allows users to share text securely and privately on the Tor network. Insights like these help researchers and advocates understand how and why Tor is being used.