
Still, download the Tor browser from its official website only and nowhere else so your computer doesn’t get any spyware or malware. The Internet is an extensive network of millions of servers, databases, and web pages that run continuously. Think of it as an iceberg, with only a tiny part visible above the surface. If you dig deeper, you’ll discover the mysterious world of the deep web and, for the brave ones, the foreboding dark web.
How To Use The Resetter Adjustment Program Epson L15150 And Save Service Costs
NordVPN responded aggressively by upgrading its entire infrastructure to RAM-only servers and ending its reliance on rented servers. It also introduced a bug bounty program, hired a cybersecurity consulting firm to test its infrastructure, and then carried out a third-party security audit. By proactively employing these detailed, actionable security measures, you can confidently mitigate risks and safely utilize the dark web while preserving your privacy and anonymity in 2025. Governments worldwide have intensified online surveillance in the name of national security, while corporations increasingly monetize personal data. As digital rights erode, anonymity online is becoming a necessity rather than a luxury for many individuals. Although the use of the mega darknet is not illegal per se, specific activities within this space may violate the law.
How To Access The Dark Web Safely Using A VPN
Many reputable websites and news outlets like ProPublica and SecureDrop often share official domain addresses of onion sites on their pages. Some users also share links on encrypted apps like Telegram or Keybase that you can check. Another website is Dread, which is often called the “Reddit of the Dark Web.” It’s a community platform where users can discuss new markets, share onion links, add reviews, and much more. If you’re lucky enough, you can find it on clearnet privacy forums. RiseUp is a top dark web website that offers secure email services and a chat option. It was created in 1999 as a secure communication platform for people and groups working on liberatory social change.
What To Do If You See Something Illegal
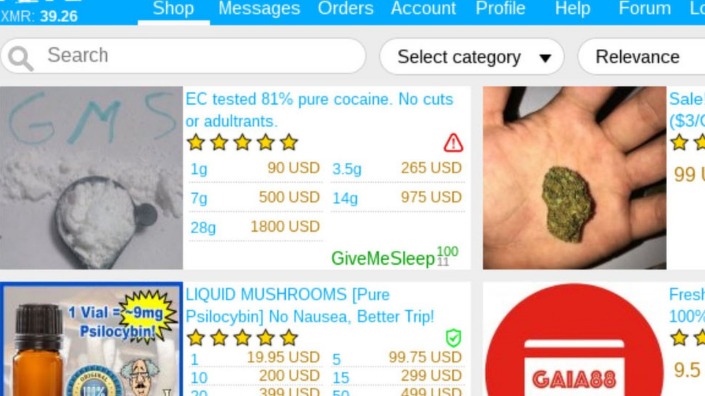
Thus, use the best antivirus software that protects against these online threats. The Silk Road was a famous dark web marketplace where users could buy and sell goods and services anonymously. All the payments were made through cryptocurrency, further enhancing marketplace anonymity. The users on this site can review and rate the products that promote reliable and fraudster vendors.
My dedication to continuous learning fuels my passion for delving into the complexities of the cyber world. And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics. Fortunately, in Hidden Wiki, every website is followed by a brief description so that the user knows what to expect. You can also take a look at the blogs & essays section if you want to find some nifty coding resources. At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen.

For Using The Internet Anonymously
This process also prevents your ISP from seeing your data or where it’s going. Since the ISP can’t detect you’re accessing dark web URLs, it won’t trigger any alarms about your online activity. For this reason, many people prefer to use a VPN to encrypt their connection to the Tor network, thereby preventing their ISP from being able to detect that they are accessing the dark web. There’s plenty of illegal content, products, and services available on the dark web. Anonymity doesn’t make carrying out illegal acts any more permissible, so be cautious about making purchases or downloading content. Mullvad is one of the few providers that offer the VPN Over Tor configuration to access the dark web.
Dark Web Chat/Social Networks
- The dark web serves as a platform where activists can organize gatherings in secret, without the fear of giving away their plans or position to the government.
- Knowing about various types of ransomware and common hacks can help you better prepare to spot cybersecurity threats on the dark web.
- If a seller encourages you to opt for other well-known and commonly used payment methods, then the person is likely to be a scammer, and you must not make any deal with them.
- Saheed earned his degree in Technology and Ethics from the University of Lagos in Nigeria.
You, or data about you, could already be at all three levels of the internet – and this should concern you. It’s not that Tor is evil; it’s just that the same tools that protect political dissidents are pretty good at protecting criminals too. No one knows precisely how many dark web sites there are out there. Tor is designed to be resistant to web crawling but the number of active ones probably only number in the thousands. Still, this open and cataloged “crawled” web content is still estimated to make up less than 1% of the internet.
CSO Executive Sessions: How AI And LLMs Are Affecting Security In The Financial Services Industry
Attempting to even view these can be illegal in many countries and states, so stay well clear of them if you want to keep a clean record and conscience. The dark web — aka, the deep web — is the second layer of the internet, which is not indexed by search engines. Websites and pages in the deep web might include password-protected content, private forums, and personalized resources. Given the many cyber threats present on the dark web, it’s recommended to be extra careful when you access it. The dark web presents various threats, including malicious software and computer viruses, posing risks to users’ systems and data security.
Tor relays are servers run by volunteers, designed to keep your activities private and untraceable. Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny. The US Supreme Court has indicated that even casual browsing could lead to legal consequences. Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS.
Having JavaScript enabled on the dark web can cause havoc because it can reveal your IP address to your website. Also, previously, the Tor browser was vulnerable to JavaScript attacks as it provided hackers a pathway to track your activities by using the session details. Therefore, for security reasons, disable JavaScript on the Tor browser and enjoy an anonymous browsing experience on the dark net.
- Even completing a transaction is no guarantee that the goods will arrive.
- Using a VPN alongside Tor adds an extra layer of security by hiding your IP address from Tor entry nodes and encrypting your traffic.
- As dark web websites are not moderated, they can host a wide range of malware, such as ransomware, keylogger, and remote access Trojan.
- Upon opening the Tor website, you will be presented with various download options for the operating systems that Tor supports, including Windows, macOS, Linux, and Android.
- Even people with little to no knowledge can buy ready-made ransomware and launch attacks on their victims.
This helps support our work, but does not affect what we cover or how, and it does not affect the price you pay. Neither ZDNET nor the author are compensated for these independent reviews. Indeed, we follow strict guidelines that ensure our editorial content is never influenced by advertisers. As previously mentioned, the dark web is not just used for criminal activities. Admittedly, studies have proven that criminal content does make up a large proportion of the dark web.
Official Security Advisories And Documentation
The Tor network began as an anonymous communications channel, and it still serves a valuable purpose in helping people communicate in environments that are hostile to free speech. “A lot of people use it in countries where there’s eavesdropping or where internet access is criminalized,” Tiquet said. The terms “deep web” and “dark web” are sometimes used interchangeably, but they are not the same. Deep web refers to anything on the internet that is not indexed by and, therefore, accessible via a search engine like Google.
BidenCash is another latest marketplace that started in 2022, and is now home to sensitive financial data transactions. This is where cybercriminals go to buy and sell things like stolen credit card numbers, personally identifiable information (PII), and even SSH login details. One thing that distinguishes BidenCash on the dark web, however, is how it markets itself. Exodus Marketplace started to become popular after the shutdown of Genesis Market, and it replaced it successfully. It claims to control more than 7,000 bots from 190+ countries, with data prices ranging from $3 to $10, based on the quality it offers. The marketplace has a simple interface, lets users filter logs easily, and accepts Bitcoin, Monero, and Litecoin for payments.



